Ph.D. Progress Report
Designing for
the Unspoken
Tacit Knowledge Transfer in
High-Stress Environments
Iren Irbe
November 2025
Technical Implementation
Voice-Controlled Auditory Learning Assistant Based on GraphRAG
(Graph Retrieval-Augmented Generation)
Problem 1: Tacit Knowledge Is Difficult to Capture and Transfer
During onboarding and offboarding, organizations struggle to retain and pass on employees’ unspoken, experience-based knowledge because it is rarely written down and hard to share.
Research Aim
To develop and evaluate a theoretical and technological approach for capturing, externalizing, and transferring tacit knowledge in high-stress public-sector environments.
The research investigates how a voice-controlled, GraphRAG-powered assistant can help preserve and reuse this hidden expertise through natural interaction and contextual learning support.
Tacit Knowledge
Michael Polanyi (1966) defined tacit knowledge as understanding that is "inherently difficult to articulate," summarized in his aphorism:
"We can know more than we can tell."
It encompasses know-how, mental models, and intuitions gained through action and experience.
The Transfer Challenge
Von Hippel (1994) coined the term "sticky information" to describe knowledge that is costly to transfer because it is context-dependent.
Tacit knowledge demonstrates this stickiness: its transfer relies on social interaction, observation, and shared experience rather than documentation.
Problem 2: Operational Pressures Prevent Tacit Knowledge Transfer
Data volume has overwhelmed traditional mentorship models.
The Big Data Reality
Agencies process over 10,000 hours of video every day.
80% of evidence is unstructured data (Europol, 2024).
The Human Consequence
Senior analysts spend 90% of their time on routine data processing.
The "Master-Apprentice" model requires time that no longer exists.
The Cognitive Bottleneck
Analysts’ valuable intuition gets buried under routine data work. Without AI to handle the repetitive tasks, there’s no time left for the human interaction needed to transfer tacit knowledge.
Situated Learning
Brown, Collins & Duguid (1989) established that knowledge is inseparable from the activity, context, and culture in which it develops.
The "Master-Apprentice" model depends on legitimate peripheral participation: novices learn by working alongside experts in authentic contexts.
Information Overload
Miller (1956) established that human working memory can hold approximately 7±2 items simultaneously.
When data volume exceeds this capacity, processing degrades. Modern intelligence environments routinely exceed these limits, creating the "cognitive bottleneck."
Presenter Notes
- Start with the sheer volume: 10k hours/day is unmanageable manually.
- Highlight the 10x growth in case data size (100GB to 1TB).
- Connect this to the "death of mentorship": seniors are too busy processing data to teach juniors.
- Use Miller's law to explain why this breaks the human brain (cognitive overload).
- Conclude with the bottleneck: AI is needed not just for speed, but to free up human capacity for tacit transfer.
Problem 3: Institutional Knowledge Disappears Faster Than It Can Be Replaced
The "Silver Tsunami" creates a knowledge vacuum that money cannot fill.
The Experience Gap
It takes 5–7 years of field experience to rebuild operational competence.
The Tangible Cost
6–8× Annual Salary
Direct training, recruitment, reduced productivity during ramp-up, supervision burden, and error costs.
The Intangible Cost
"Deep Smarts"
Unwritten heuristics, informant networks, and pattern recognition that are never documented in SOPs.
Why "Writing It Down" Is Insufficient
The Curse of Knowledge (Hinds, 1999): Experts systematically underestimate how difficult tasks are for novices because they cannot "un-know" what they have learned. They often fail to articulate the critical "why" behind their decisions because it feels obvious to them.
Deep Smarts (Leonard, 2005)
Expert intuition built through years of experience: pattern recognition, judgment under uncertainty, and contextual awareness.
Unlike explicit knowledge in manuals, deep smarts are transferred through guided experience and Socratic dialogue.
Inheritance Imperative
Hang & Zhang (2024) argue that when experts retire, organizations face a "knowledge inheritance crisis."
Departing expert knowledge is organizational inheritance that must be actively claimed through structured protocols.
Recognition-Primed Decision
Klein (1993) showed that experts do not deliberate options; they recognize patterns.
TacitFlow preserves these pattern libraries by capturing the cues experts notice.
Workforce Crisis
- OECD (2025): 40% of civil servants report burnout; 13% intend to leave within 12 months.
- Europol (2025): Urgent need for "state-of-the-art analytical competence" to address capability gaps.
Presenter Notes
- Hook: The "Silver Tsunami" isn't just about empty desks; it's about empty minds.
- Visual: Point to the gap. 20 years vs 2 months. That gap is where mistakes happen.
- Theory: Briefly mention "Deep Smarts" - it's not magic, it's pattern recognition (Klein).
- Problem: Explain "Curse of Knowledge" - experts can't teach this easily because they've forgotten what it's like not to know.
- Solution Tease: A system is needed that extracts this "obvious" knowledge before they leave.
Problem 4: Existing AI Cannot Be Used to Solve These Challenges
Security and reliability constraints rule out commercial solutions.
Why not just use ChatGPT? Because intelligence work operates under constraints that commercial AI cannot meet.
1. Sovereignty & Secrecy
Commercial clouds (e.g., OpenAI, Azure) are legally incompatible with Classified/RESTRICTED data due to jurisdiction risks (CLOUD Act). Data cannot leave the building.
2. The Hallucination Risk
Generative models invent facts. In a legal context, a single hallucination renders evidence inadmissible. The approach prioritizes Groundedness over creativity.
3. The Provenance Gap
"Black box" answers are useless in court. Intelligence requires a Chain of Custody for reasoning. This means knowing exactly which document led to which conclusion.
"The solution requires the power of LLMs without the risk of the Cloud or the unreliability of generation."
LLMs generate plausible-sounding but factually incorrect information because they predict tokens based on statistical patterns rather than verified facts. TacitFlow mitigates this via Retrieval-Augmented Generation (RAG). (Lewis et al., 2020)
The property ensuring AI outputs are anchored in verifiable source material. Unlike creative text generation, grounded reasoning requires every claim to trace back to documented evidence.
W3C PROV-O (2013) provides the standard vocabulary for expressing provenance. TacitFlow uses PROV-O to maintain digital chain-of-custody, tracking who generated information, from what sources, through which processes.
- Address the "Build vs. Buy" question immediately.
- Emphasize that the project isn't building an LLM from scratch (too expensive), but can't use off-the-shelf ChatGPT (too risky).
- The "Hallucination" point is critical for legal admissibility. One error poisons the case.
- Explain the "Black Box" problem: judges need to know why an AI thinks a suspect is guilty.
Research Outputs
A portfolio of theoretical, empirical, and technical contributions.
| Status | Type | Title / Context |
|---|---|---|
| Published | Conf. Paper | "Designing for the Unspoken: A Work-in-Progress on Tacit Knowledge Transfer in High-Stress Public Institutions" (Irbe & Ogunyemi, 2025) |
| Published | Conf. Poster | "Investigating Tacit Knowledge Transfer in Public Sector Workplaces" (Irbe, 2025c) |
| In Review | Journal Article | "Capturing and transferring tacit knowledge: A scoping review" (Irbe, 2025a) |
| In Review | Journal Article | "Workplace Learning article" |
| Ready | Journal Article | "Knowledge sharing in high-stress public sector organizations: An exploratory study" (Target: J. of Knowledge Mgmt) |
| Draft | Theory Report | "From Intuition to Inference: An Approach for Implementing Tacit Knowledge Transfer" |
| Draft | Technical Report | "TacitFlow: A Voice-Controlled AI Assistant for Tacit Knowledge Transfer" |
The research follows a multi-pronged approach: establishing the theoretical gap (Scoping Review), validating the problem (Empirical Study), and proposing the solution (Technical Report).
Targeting high-impact journals in Knowledge Management and AI to bridge the gap between social science theory and technical implementation.
- This slide establishes academic rigor.
- Highlight the progression: Scoping Review -> Empirical Study -> Technical Implementation.
- Mention that the "In Review" articles are the core theoretical contributions.
- The "Draft" reports are the basis for this presentation and the prototype.
Research Questions
Three questions guide this doctoral research, each addressed through distinct methodological approaches.
What current methods are used to capture and transfer tacit knowledge?
Method: Scoping Review
What are the primary barriers and enablers that affect tacit knowledge sharing practices?
Method: Interview Study
What are the current research trends and gaps in the field of tacit knowledge management?
Method: Scoping Review
How can AI-mediated systems support tacit knowledge transfer in high-stress public sector environments?
Method: Software as Hypothesis
Emerging / Ill-defined* This question is intentionally open-ended. It will be refined based on the pilot validation results.
This study employs Design-Based Research (DBR), iterating between theory and practice to develop a working artifact. DBR bridges the gap between laboratory findings and real-world practice. (Wang & Hannafin, 2005)
RQ4 is an "emergent" question. In DBR, the intervention itself (TacitFlow) acts as a hypothesis. The study tests if the existence of such a tool changes the nature of the problem.
- RQ1 & RQ3 are theoretical foundations (the "What" and "Where").
- RQ2 is the empirical validation (the "Why not").
- RQ4 is the constructive contribution (the "How").
- Emphasize that RQ4 is not just about building software, but using software to probe the theoretical limits of tacit knowledge transfer.
Research Flow
From literature to prototype: a Design-Based Research trajectory.
Scoping Review
Analyzed 55 papers on tacit knowledge transfer and workplace learning to establish the theoretical baseline.
Interviews & Analysis
Conducted semi-structured interviews with 10 experts from high-stress public institutions to validate the problem space.
Key Findings
Identified that informal sharing is critical but fragile, often lost due to turnover and lack of structured capture mechanisms.
Early Prototype (TacitFlow)
Developed a voice-based AI assistant as a "Research Through Design" artifact to probe the feasibility of capture.
Next Steps
Co-design, evaluation, and testing through participatory design sessions with end-users.
Artifacts embody theoretical propositions. The prototype becomes a vehicle for testing ideas rather than merely an end product. (Zimmerman, Forlizzi & Evenson, 2007)
Building systems specifically to validate theoretical constructs. TacitFlow is not a commercial product but a research instrument for testing the EASCI framework. (Leinonen et al., 2008)
- Walk through the timeline chronologically.
- Highlight that the project is currently at Step 4 (Prototype).
- Use the side notes to defend the "building software" part of a PhD. It's a methodological choice, not just engineering.
Scoping Review
Understanding how tacit knowledge is captured and transferred in organizations
This review examined methods, barriers, and enablers for organizational experience-sharing, with particular attention to transitions (onboarding/offboarding) in complex institutional settings.
| Parameter | Description |
|---|---|
| Corpus | 55 peer-reviewed studies + monographs (2019–2024) |
| Framework | Arksey & O'Malley (2005); PRISMA-ScR |
| Databases | Scopus, Web of Science, Google Scholar |
| Keywords | tacit knowledge · onboarding · offboarding · informal learning · public sector |
| Exclusion | Formal training & general KM systems only |
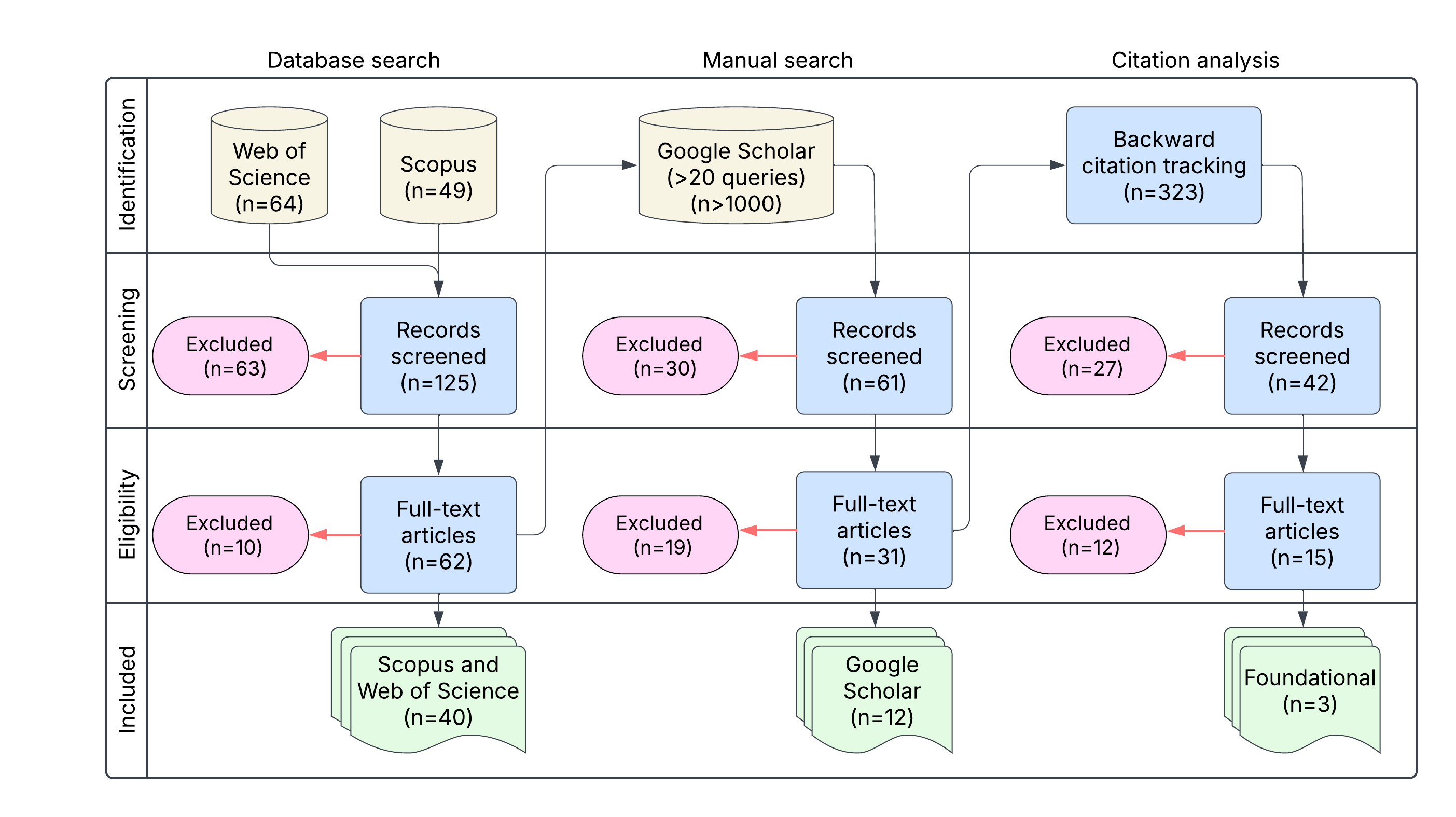
Methodology
Arksey & O'Malley (2005) established the framework for scoping reviews, distinguishing them from systematic reviews by their broader exploratory purpose. Scoping reviews map key concepts, evidence types, and research gaps rather than synthesizing effect sizes.
PRISMA-ScR
Tricco et al. (2018) extended PRISMA reporting guidelines specifically for scoping reviews, adding items on rationale for review type selection and deviation from protocol. This enhances transparency and reproducibility in exploratory evidence synthesis.
Presenter Notes
- Emphasize the rigor: 55 studies selected from a much larger pool.
- Highlight the specific focus on "transitions" (onboarding/offboarding) as critical moments for tacit knowledge loss.
- Explain the exclusion of "formal training" - the focus is on the unspoken and informal aspects of knowledge transfer.
- The PRISMA flow diagram (right) visually demonstrates the filtering process.
Key Findings from Scoping Review
Barriers, Enablers, and the Human-Centric Reality
Tacit knowledge transfer remains a deeply human-centered process. The most significant barriers are organizational, not technical. A gap exists at the "Externalization" stage; technology plays only a supplementary role.
Barriers vs. Enablers
Barriers
- •Lack of trust between colleagues
- •Limited time for knowledge sharing
- •Weak knowledge-sharing culture
- •No clear structure for transfer
Enablers
- •Strong interpersonal relationships
- •Open organizational culture
- •Supportive leadership
- •Psychological safety
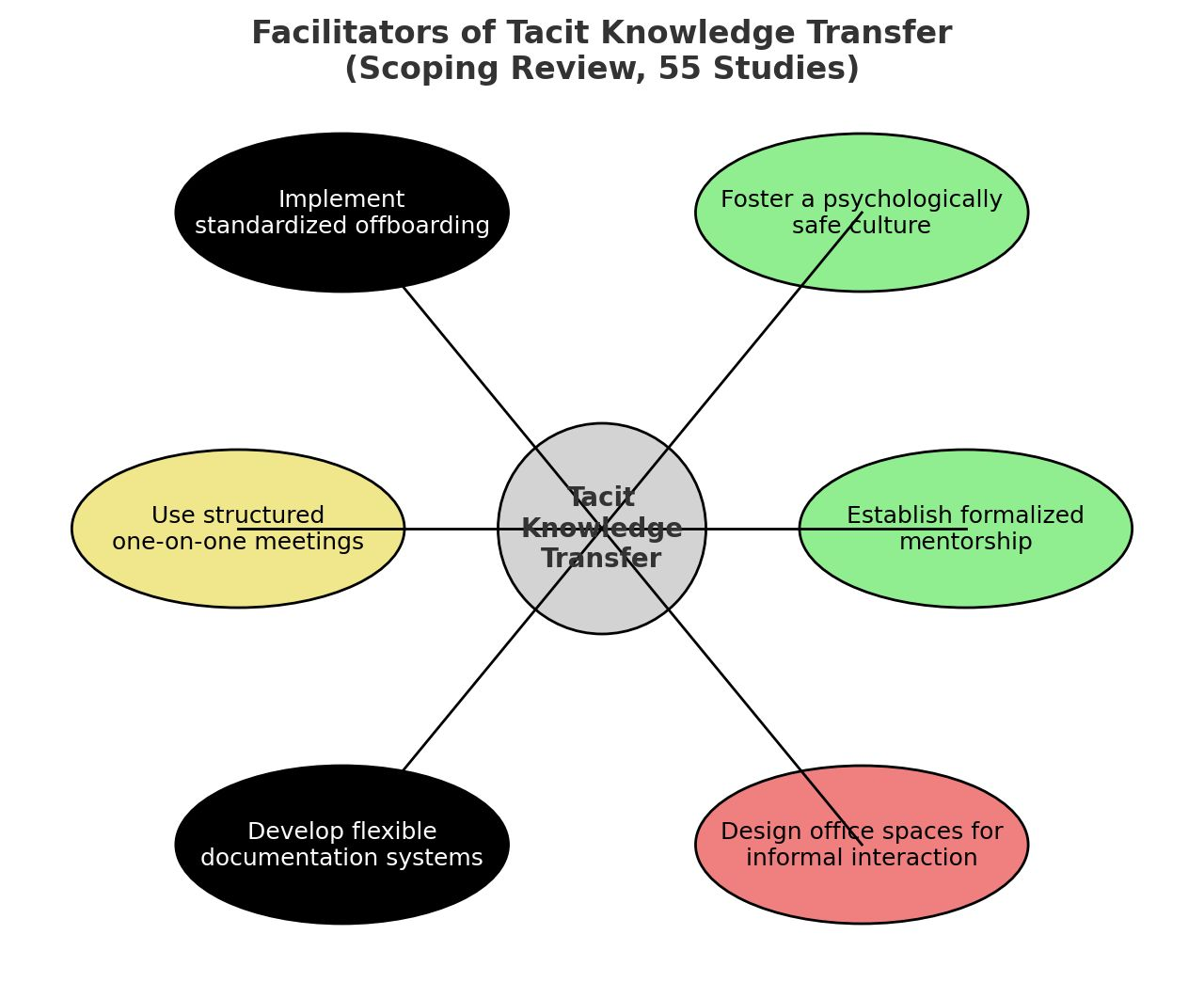
The Externalization Gap
The SECI model assumes externalization is straightforward. The review found the opposite: converting tacit knowledge to explicit form is the primary bottleneck in knowledge transfer.
Key Insight
A gap exists between how people share knowledge in practice (socially) and how technology supports it (structurally).
Detailed Findings
Most workplaces rely on mentoring, storytelling, and job shadowing. AI or digital tools for experience sharing remain rare. While socialization methods are common, they rarely succeed in making tacit knowledge explicit.
Presenter Notes
- Discuss the "Externalization Gap" - this is where TacitFlow aims to intervene.
- Note the color coding: Green (Social) factors are enablers, while Gray/Yellow (Org/Structural) are often barriers.
- The diagram (Figure 3) synthesizes these factors into a holistic view of the transfer environment.
Interview-Based Empirical Study
Knowledge sharing in high-stress public sector organizations
| Dimension | Details |
|---|---|
| Goal | Explore real onboarding/offboarding practices in high-stress public institutions. |
| Participants | 10 professionals (6 managers, 4 specialists) across 6 Estonian organizations. |
| Approach | Semi-structured interviews (45-90 min) + Thematic Analysis. |
| Coding | Hybrid deductive-inductive approach (Braun & Clarke, 2006). |
"Knowledge transfer in organizations usually relies on informal and unstructured practices, such as spontaneous (ad hoc) mentoring or casual peer-to-peer storytelling."
Key Empirical Finding
Organizations rely heavily on informal practices because formal systems fail to capture experience-based judgment. Barriers include lack of psychological safety, isolated workspaces, outdated documentation, and missing offboarding procedures. These are precisely the gaps EASCI addresses.
Thematic Analysis
Braun & Clarke (2006) established thematic analysis as a qualitative method. Their six-phase process (familiarization, coding, theme generation, review, definition, write-up) enables systematic pattern identification while remaining accessible. Unlike grounded theory, it permits both inductive and deductive coding.
From Interviews to EASCI
This study revealed that tacit-to-explicit conversion does not happen in one leap (as SECI suggests). Interview data showed knowledge transfer requires multiple deliberate stages: initial recognition of experience, tentative articulation, structured formalization, social validation, and adaptive refinement.
Participating Organizations
- EASS: Estonian Academy of Security Sciences
- KRA: Defence Resources Agency
- MoD: Ministry of Defence
- PBGB: Police & Border Guard Board
- RIA: Information System Authority
- SMIT: IT & Development Centre
Presenter Notes
- Interviews were conducted with 10 professionals from high-stress environments (Police, Defense, IT).
- Used Braun & Clarke's thematic analysis to identify patterns.
- Crucial Insight: The "leap" from tacit to explicit is too big for a single step. It requires a staged approach.
- This empirical evidence directly informed the 5-stage EASCI framework discussed next.
Interview Findings
Tacit knowledge in Estonian public sector organizations
When experienced personnel depart, they take "sticky" tacit knowledge with them. This knowledge is embedded in intuition, informal routines, and "gut feelings" rarely captured in formal manuals.
Key Observations
- Informal Sharing Relies on mentoring, teamwork, and social interaction.
- Weak Capture Experience stays in heads; systematic capture is rare.
- Barriers Stress, time pressure, lack of structure & safe spaces.
- Enablers Trust, open culture, and psychological safety.
- Offboarding Often unplanned, unstructured, and rushed.
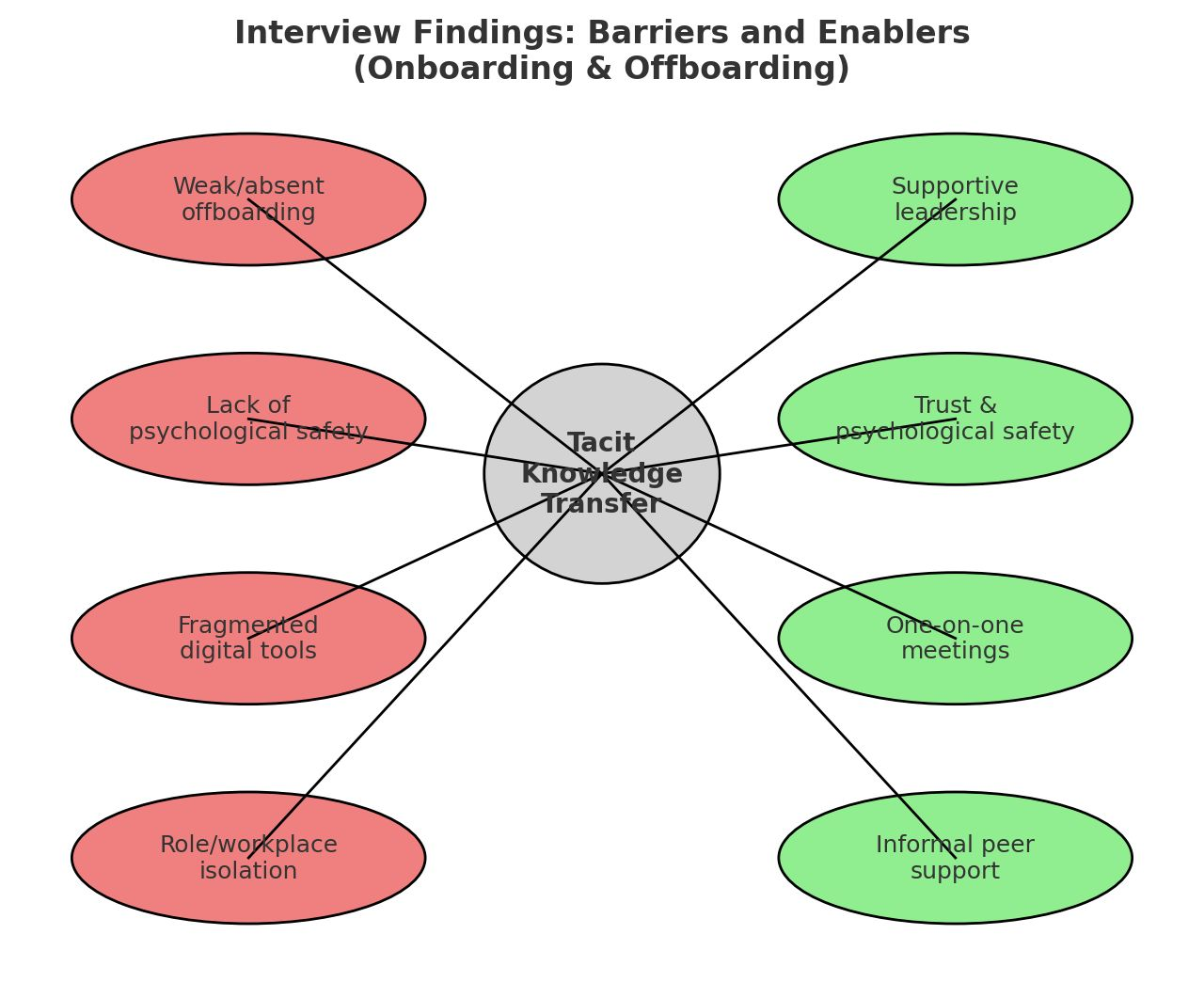
"Sticky" Tacit Knowledge
Von Hippel (1994) coined "sticky information" to describe knowledge costly to transfer. Tacit knowledge is deeply embedded in context, making it resistant to codification.
Current Mechanisms
Transfer relies on ad-hoc mentoring ("watch me do this"). This breaks down during rapid turnover or when key personnel leave unexpectedly.
Practitioner Interest
Participants expressed strong preference for tools making sharing easier. Voice-based AI assistants resonated well for quick, natural capture.
Presenter Notes
- Define "Sticky Knowledge" - it costs money and time to move it.
- Point out the red bars in the list: Barriers and Offboarding are major pain points.
- The diagram shows the environment where this happens.
- Mention the "Voice AI" finding - this validates the technical approach later.
The Externalization Gap
Where knowledge transfer fails in practice
Core Finding: Organizations succeed at Socialization (sharing experience) but fail at Externalization (converting experience into reusable knowledge).
Evidence: Scoping Review
Of 55 studies analyzed, most focus on socialization methods. Few address how technology can support externalization.
Gap: Theoretical & Technological
Evidence: Field Interviews
Across 10 practitioners, strong informal sharing cultures exist, but knowledge vanishes when experts depart.
Gap: Practical & Organizational
Research Direction: Dual Gap Convergence
The theoretical gap (missing models) and practical gap (missing processes) converge on a single need: tools that transform spoken experience into preserved, reusable knowledge. This points toward voice-based solutions that align with how experts naturally articulate experience.
SECI Model Context
Nonaka & Takeuchi (1995) describe four knowledge conversion modes. While organizations excel at Socialization (mentoring), they struggle with Externalization (articulating concepts).
Convergent Validity
Literature and field data independently identify the same failure point, strengthening confidence in this finding.
Documented Loss
Cho et al. (2020) documented this in Security Operations Centers: tacit expertise remains "trapped in heads" until personnel depart, then vanishes.
Presenter Notes
- This slide is the "Pivot Point" of the presentation.
- The problem has been identified (Tacit Knowledge Loss) and the specific mechanism of failure (Externalization).
- The visual flow makes it obvious: humans are good at talking (Socialization) but bad at capturing (Externalization).
- This sets up the solution: TacitFlow is an Externalization Engine.
TacitFlow Prototype: Concept and Features
A voice-controlled AI assistant for capturing and retrieving tacit knowledge
Based on interview findings, TacitFlow is being developed as an AI voice assistant that captures and connects everyday experience so it can be reused by others.
Core Functionality
- Capture Speak out short experiences, tips, or lessons.
- Store Save automatically as searchable knowledge.
- Retrieve Get spoken answers, contextual suggestions, or text search results.
Knowledge Object Output
Captured speech becomes structured data:
- Searchable Transcription: Full text index.
- Semantic Tags: Automated categorization.
- Source Attribution: Context & provenance.
- Confidence Scores: AI processing metadata.
Target Use Cases
- 1. Retirement Capture: Preserving senior personnel expertise before they leave.
- 2. Accelerated Onboarding: Reducing the competence-building period for new hires.
- 3. Operational Debriefs: Capturing lessons immediately after incidents.
- 4. Cross-Institutional Sharing: Making tacit knowledge searchable across silos.
- 5. Research Platform: Testing theoretical assumptions about AI mediation.
Why Voice?
- Natural: Experts articulate experience through storytelling.
- Focus: Speaking allows capture without breaking concentration.
- Context: Voice preserves narrative structure and reasoning.
Software as Hypothesis
TacitFlow is a research instrument (Leinonen et al., 2008). It operationalizes concepts from knowledge management theory to allow empirical validation. The study tests: Can AI mediate the tacit-to-explicit conversion?
Workflow Integration
TacitFlow requires no separate login or forms. It integrates into existing work activities, capturing knowledge through passive listening or brief voice prompts.
Presenter Notes
- Introduce TacitFlow as the direct response to the "Externalization Gap".
- Highlight the "Voice First" approach - it's not just a feature, it's the core design philosophy to lower friction.
- Walk through the 3 steps: Capture, Store, Retrieve.
- Emphasize that this is "Software as Hypothesis" - it was built to test the theory.
SECI Model
The dominant theoretical framework for organizational knowledge creation
Before examining why the Externalization Gap exists, one must understand the theoretical framework that defines it. Nonaka & Takeuchi (1995) proposed the SECI model as a continuous spiral of knowledge conversion between tacit and explicit forms.
The Four Conversion Modes
- Socialization
- Tacit → Tacit Sharing through experience: apprenticeship, mentoring, shadowing.
- Externalization
- Tacit → Explicit Articulating concepts into shareable form. The critical bottleneck.
- Combination
- Explicit → Explicit Systemizing knowledge into documents, databases, procedures.
- Internalization
- Explicit → Tacit Learning by doing; explicit knowledge becomes embodied skill.
Research Starting Point
The research started with the SECI model, but its main weakness quickly became clear in high-stress environments: it assumes that Externalization will happen if people simply try hard enough.
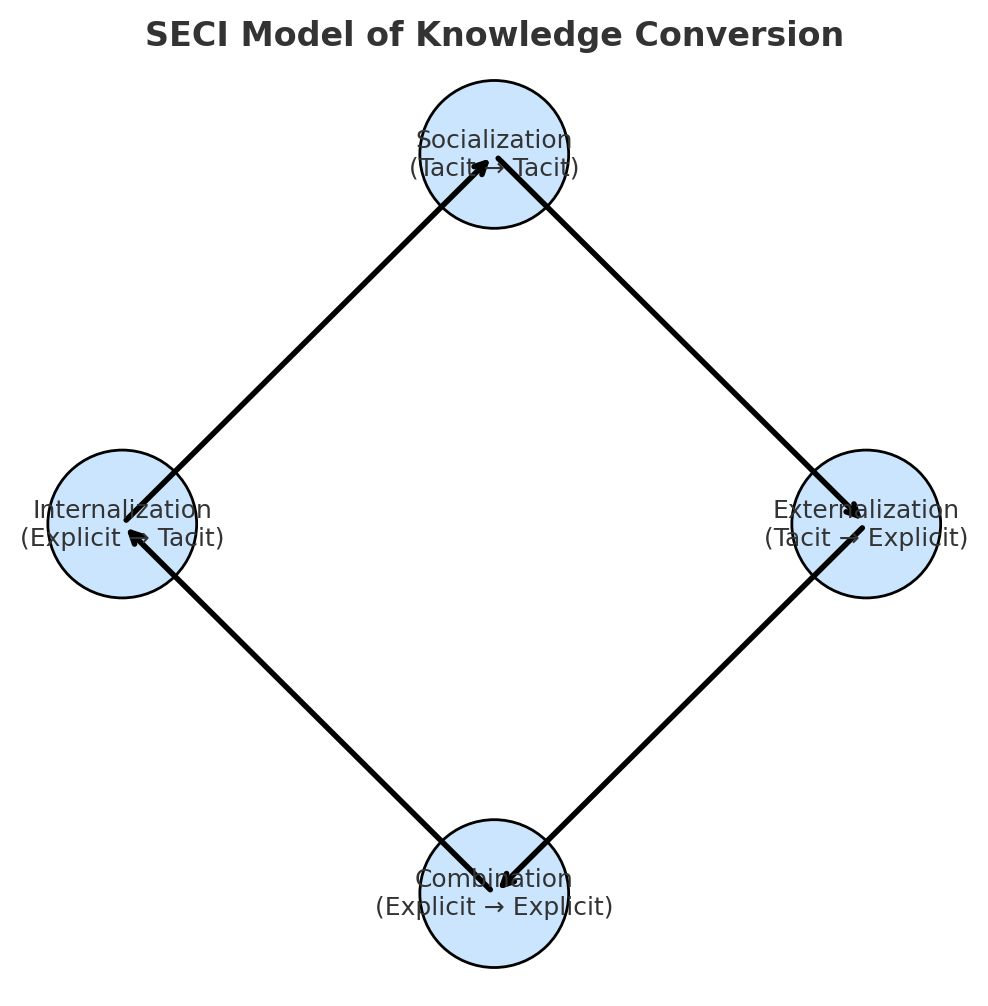
Why SECI?
Nonaka and Takeuchi's The Knowledge-Creating Company (1995) is among the most cited works in management science. SECI has shaped knowledge management practice for three decades.
The Spiral Concept
SECI operates as a continuous spiral rather than a linear sequence. Knowledge cycles through all four modes repeatedly.
Academic Critiques
- Gourlay (2006): Externalization lacks operational definition. It's a metaphor without a mechanism.
- Tsoukas (2003): Tacit knowledge cannot be fully "converted". It remains context-dependent.
- Snowden (2002): SECI oversimplifies context, assuming universal applicability.
Presenter Notes
- Briefly explain the 4 quadrants. Don't get bogged down in theory, but establish the vocabulary.
- Focus on the Red Quadrant (Externalization): This is where the magic is supposed to happen, but often doesn't.
- Mention the critiques: The project isn't the first to say SECI is imperfect, but it proposes a specific fix for the Externalization step.
The Limits of SECI in High-Stress Environments
Why the "Knowledge Spiral" Breaks Down Under Pressure
SECI assumes Externalization occurs naturally given sufficient motivation. It describes that conversion happens, not how. This lack of operational mechanism causes failure in high-stress contexts.
The Core Problem
- Operational Gap SECI describes process, not mechanism. It offers a metaphor without a method for extraction.
- High-Stress Failure Standard interventions (e.g., "lessons learned") fail when investigators cannot articulate "gut feel" pattern matching.
Why SECI Fails for AI
- Context Blindness SECI relies on shared physical space (Ba). AI lacks this "situated cognition."
- The Articulation Gap Metaphor is insufficient for code. AI needs structured "Intuition Pumps" to elicit reasoning.
- Missing Verification SECI relies on social consensus. AI needs explicit "Quality Gates" to prevent hallucination.
EASCI: Operationalizing SECI
Where SECI offers a metaphor, EASCI supplies the engineering: specific protocols for externalization, quality gates for verification, and AI mediation for structure.
"We know more than we can tell."
— Michael Polanyi (1966)
Collins' Taxonomy (2010)
- Relational: Concealed by social dynamics.
- Somatic: Physically embodied skill.
- Collective: Distributed across a team.
Theoretical Limits
- Gourlay (2006): "Externalization" lacks operational definition.
- Tsoukas (2003): Context is inseparable from tacit knowledge.
- Von Hippel (1994): "Sticky information" resists transfer.
Presenter Notes
- Start with the Polanyi quote: it's the fundamental truth of this domain.
- Explain that SECI works fine for "business as usual" but breaks when things get chaotic.
- Key Point: AI cannot just "absorb" culture like a human apprentice. It needs explicit structures.
- Introduce EASCI as the "engineering fix" to SECI's "theoretical bug."
SECI Model: The Externalization Gap
Why SECI proved insufficient as a blueprint for system design
Scoping Review, Interviews, and Theoretical Analysis showed the same problem: SECI helps people build trust, but it does not help them express complex, experience-based knowledge.
Theoretical Failures
- Articulation Barrier Tacit knowledge is hard to explain. "We know more than we can tell."
- Mechanism Gap "Externalization" is a metaphor, not a process. No operational definition exists.
- Missing Cognition SECI ignores inference. Abduction and intuition pumps are required.
Example: Intuition Pump
"Imagine a new colleague is about to handle their first high-pressure incident alone. What's the one thing you'd want them to know that isn't in any manual?"
This bypasses the "what do you know?" block by creating a concrete, protective scenario.
"SECI was not enough for building a real system because it doesn’t explain how tacit knowledge becomes explicit. It describes the idea but not the mechanism."
Abductive Reasoning
Peirce (1903): The process of forming explanatory hypotheses. Unlike deduction (proving) or induction (generalizing), abduction infers the best explanation for a specific situation.
Intuition Pumps
Dennett (2013): Thought experiments designed to elicit intuitions. They bypass the Polanyi Paradox by asking "what would you do if...?" rather than "what do you know?".
Key References
- Polanyi (1966): The Tacit Dimension.
- Gourlay (2006): "Conceptualizing Knowledge Creation."
- Busch (2008): "Tacit Knowledge in Organizational Learning."
Presenter Notes
- Walk through the flow diagram: Green works, Red is broken.
- Explain why it's broken: The "Mechanism Gap."
- Use the "Intuition Pump" example to show how the system fixes it. Instead of asking "tell me what you know," the system asks "what would you tell a rookie?"
- This shift from direct questioning to scenario-based elicitation is the core of the approach.
The Role of AI in Tacit Knowledge Capture
Can a voice-controlled agent help externalize tacit knowledge?
The Externalization Problem
Tacit knowledge externalization fails because experts cannot easily verbalize what they know. Polanyi (1966) describes this as "we know more than we can tell." This is compounded by the Curse of Knowledge (Hinds, 1999): experts struggle to imagine what novices don't know, making direct transfer ineffective. Interview findings confirm that experts struggle to articulate reasoning under time pressure.
Socratic Mediation
TacitFlow does not replace human reasoning; it acts as a Socratic interviewer that prompts reflection and forces articulation (Dennett, 2013: intuition pumps; Dewey, 1938: inquiry as reflective practice). This differs from retrieval-augmented generation: the AI elicits rather than merely retrieves.
Why Not Traditional KM?
Traditional KM tools cannot support abductive or narrative reasoning (Gourlay, 2006; Collins, 2010). AI agents can observe interaction patterns, ask clarifying questions, and assist in forming structured Knowledge Objects, shifting from passive storage to active mediation.
Research Through Design
The methodological foundation is Research Through Design (Zimmerman, Forlizzi & Evenson, 2007), where the system is built to test theoretical assumptions. Leinonen et al. (2008) describe this as "Software as Hypothesis": a prototype used to validate theoretical constructs, not a commercial product.
This theoretical position creates the bridge to the EASCI framework.
The Socratic Method
Named after Socrates (470-399 BCE), the method uses guided questioning rather than direct instruction. The teacher asks probing questions that expose contradictions, forcing the learner to refine their understanding. TacitFlow's AI probes follow this tradition: asking questions that help experts articulate what they know.
Iterative Refinement
DBR's iterative cycles distinguish it from traditional experiments. Each TacitFlow iteration generates usage data that informs the next design phase, embodying DBR's commitment to theory-practice integration.
Cognitive Load Theory
Sweller (1988): Working memory has strict limits. TacitFlow's voice interface minimizes extraneous load (typing/navigating) to preserve germane load (reflection/articulation).
Recognition-Primed Decision
Klein (1993): Experienced practitioners recognize patterns rather than deliberating options. TacitFlow preserves these pattern libraries by capturing the cues experts notice.
Complex Thinking
Morin (2008): Complex phenomena require multiple perspectives. TacitFlow synthesizes pragmatism, process philosophy, organizational learning, and cognitive science.
Deep Smarts
Leonard (2005): Expert intuition built through years of experience. Unlike explicit knowledge in manuals, deep smarts are transferred through guided experience and Socratic dialogue.
Psychological Safety
Edmondson (1999): Essential for sharing. Experts must feel safe revealing their "tricks" without fear of judgment. TacitFlow addresses this through anonymous draft submission and mentor-mediated validation.
Mental Models
Internal representations (e.g., "suspicious behavior"). TacitFlow captures mental models through structured articulation and makes them visible for peer validation.
Avoiding Competency Traps
March (1991): Organizations that over-exploit existing knowledge fall into "competency traps." EASCI balances exploitation (Consolidation) with exploration (Innovation).
Process Philosophy
Whitehead: Actual Entities are "drops of experience." Concrescence is the integration of data into a new unity. In TacitFlow, each Knowledge Object is a concrescence of prior data, perspective, and AI structuring.
Collins' Taxonomy (2010)
Relational: Concealed by social dynamics.
Somatic: Embodied.
Collective: Social.
TacitFlow targets relational and somatic knowledge through conversational elicitation.
Experiential Learning
Kolb (1984): Concrete Experience → Reflective Observation → Abstract Conceptualization → Active Experimentation. EASCI maps directly onto this cycle.
Miller's Law (7±2)
Working memory holds ~7 chunks. EASCI's structured stages respect this limit by processing knowledge incrementally.
Curse of Expertise
Hinds (1999): Experts cannot "unlearn" expertise to imagine a beginner's perspective. TacitFlow's AI probes address this by asking the questions novices would ask.
Presenter Notes
- The "Why": AI is used not just to record, but to provoke.
- The "How": Socratic questioning. The AI plays the role of the "naive learner" to force the expert to explain things clearly.
- Theoretical Basis: This isn't just a tech demo; it's "Research Through Design." It was built to test if this kind of capture is even possible.
- Highlight Psychological Safety: If cops/firefighters don't feel safe, they won't talk. The system is designed for that.
A Proposed Alternative to SECI: The EASCI Framework
How TacitFlow operationalizes SECI, Pragmatism, and Process Philosophy
EASCI addresses the Externalization Gap identified in SECI. Where SECI assumes tacit-to-explicit conversion happens spontaneously, EASCI decomposes it into discrete, operationalizable stages with defined inputs, outputs, and validation criteria.
| Stage | Name | Function | Theoretical Basis |
|---|---|---|---|
| E | Experience | Context-embedded apprenticeship; learning occurs in the flow of work | Dewey, 1938; Brown et al., 1989 |
| A | Articulation | Intuition pumps & guided explanation; eliciting tacit narratives | Dennett, 2013; Polanyi, 1966 |
| S | Structuring | Abductive mapping into formal Knowledge Objects with provenance | Peirce, 1903; Simon, 1996 |
| C | Consolidation | Social verification & sensemaking before entering the canon | Weick, 1995; Walsh & Ungson, 1991 |
| I | Innovation | Smart Forgetting & knowledge evolution; pruning outdated KOs | Whitehead, 1929; Kluge & Gronau, 2018 |
Why EASCI?
SECI says tacit knowledge can be made explicit but doesn't explain the process, skipping the "how". EASCI splits this into two actions: first explaining the reasoning (Articulation), then organizing it (Structuring). This gives us a practical way to build AI that helps with each part.
Stage Mechanisms
- Experience: (Dewey) grounds knowledge in action: learning by doing, not isolation.
- Articulation: (Dennett, Polanyi) treats explanation as an elicited process requiring guided prompts.
- Structuring: (Peirce) formalizes tacit insights through abductive reasoning.
- Consolidation: (Weick) requires community sensemaking before knowledge enters the canon.
- Innovation: (Whitehead) ensures knowledge remains dynamic, allowing pruning and refinement.
Theoretical Backbone
This framework is the theoretical backbone that TacitFlow operationalizes. Each stage maps to specific system components and AI agents in the architecture.
Sensemaking (Weick, 1995)
Sensemaking is the retrospective process through which people construct "plausible accounts" of ambiguous situations. Unlike rational decision-making models, sensemaking acknowledges that meaning emerges through social interaction and narrative construction. TacitFlow's Consolidation stage operationalizes this by requiring peer dialogue before knowledge enters the canon.
Field Example
Time>02:00 + Unlocked = RiskDavid Kolb's Experiential Learning
David Kolb (1939-present) developed the Experiential Learning Theory (ELT) synthesizing work by Dewey, Lewin, and Piaget. His four-stage cycle shows learning as a spiral: (1) Concrete Experience (doing), (2) Reflective Observation (watching and reflecting), (3) Abstract Conceptualization (thinking and concluding), (4) Active Experimentation (planning and trying). Each stage requires different abilities. EASCI's five stages map directly onto Kolb's cycle with Consolidation added for social validation.
Dave Snowden's Cynefin Framework
Dave Snowden developed the Cynefin (Welsh: "habitat") framework distinguishing five domains: Simple (clear cause-effect; best practice), Complicated (expertise needed; good practice), Complex (emergent; probe-sense-respond), Chaotic (no patterns; act-sense-respond), and Disorder (unknown domain). Snowden critiqued SECI for treating all knowledge as if it existed in the "Complicated" domain. TacitFlow is designed for the Complex domain where knowledge emerges through interaction rather than transfer.
Presenter Notes
- EASCI vs SECI: Emphasize that SECI is a "what" model, EASCI is a "how" model.
- The Gap: The jump from Tacit to Explicit is the hardest part. It is split into Articulation (getting it out) and Structuring (making it useful).
- Theoretical Depth: Point out that this is grounded; it's grounded in Dewey, Peirce, Weick, etc.
- Field Example: Walk through the police example to make it concrete.
EASCI Framework: The Knowledge Lifecycle
A dynamic system with recursive feedback paths
Unlike SECI's linear progression, EASCI models knowledge as a dynamic system with multiple feedback paths.
Theoretical Backbone
This framework is the theoretical backbone that TacitFlow operationalizes. Each stage maps to specific system components and AI agents in the architecture.
Why EASCI?
SECI says tacit knowledge can be made explicit but doesn't explain the process, skipping the "how". EASCI splits this into two actions: first explaining the reasoning (Articulation), then organizing it (Structuring). This gives us a practical way to build AI that helps with each part.
Stage Mechanisms
- Experience: (Dewey) grounds knowledge in action: learning by doing, not isolation.
- Articulation: (Dennett, Polanyi) treats explanation as an elicited process requiring guided prompts.
- Structuring: (Peirce) formalizes tacit insights through abductive reasoning.
- Consolidation: (Weick) requires community sensemaking before knowledge enters the canon.
- Innovation: (Whitehead) ensures knowledge remains dynamic, allowing pruning and refinement.
Dynamic vs. Linear
SECI presents a linear spiral: Socialization → Externalization → Combination → Internalization. EASCI models knowledge as a complex adaptive system with multiple feedback loops. Innovation can trigger new Experience; Consolidation can require return to Articulation.
Process Philosophy View
Whitehead's (1929) "creative advance into novelty" reframes knowledge as flux, not static entity. What appear as stable organizations are merely "relatively stable" patterns emerging from underlying processes. EASCI embodies this dynamic view.
Process Philosophy Explained
Process philosophy treats reality as fundamentally composed of events and processes rather than static substances. Whitehead, its primary architect, argued that "actual occasions" of experience are the ultimate constituents of reality. For knowledge management, this means: knowledge is not a thing to be stored but an ongoing process of becoming. Each moment of knowing integrates past experiences into present understanding and propels toward future inquiry.
Pragmatism Explained
Pragmatism (Peirce, James, Dewey) judges ideas by their practical consequences rather than abstract truth. Knowledge is validated through action: "truth is what works." For EASCI, this means: a KO is valid if it enables effective action. The framework doesn't seek abstract truth but practical utility: knowledge that helps practitioners navigate real situations.
Why Five Stages?
Each stage transforms knowledge through specific cognitive and social mechanisms. Unlike SECI's four modes, EASCI separates Articulation from Structuring because they require different AI interventions: dialogue-based elicitation vs. abductive formalization.
Presenter Notes
- The Loop: Focus on the visual. It's not a line, it's a cycle.
- Feedback: Point out the arrows going back. You can go from Innovation back to Experience.
- Philosophy: Briefly mention Whitehead and Pragmatism. The focus is on "what works" (Pragmatism) and "knowledge as a process" (Process Philosophy).
- AI Role: The AI helps move knowledge from one stage to the next.
EASCI Stages 1-3: Capture & Structure
The Capture Phase (E-A-S)
Stages 1-3 form the "capture" phase: grounding knowledge in action, surfacing hidden assumptions, and formalizing insights into verifiable Knowledge Objects.
1. Experience (Dewey, 1938; Brown & Duguid, 1991)
Context-Embedded Apprenticeship. Knowledge is not static data but active inquiry. Learning occurs in the flow of work ("learning by doing"), not in isolation.
2. Articulation (Dennett, 1991)
Intuition Pump Scenarios. Tacit knowledge resists direct questioning. The system uses "intuition pumps": thought experiments and counterfactuals to force the narration of hidden assumptions. This captures the why behind decisions.
3. Structuring (Peirce, 1903)
Abductive Mapping. Moving from "hunches" to hypotheses. Peirce's abduction is used to structure uncertain insights into formal "Knowledge Objects" (KOs) with provenance.
Why Three Stages for Capture?
SECI assumes tacit-to-explicit conversion happens spontaneously. EASCI decomposes this into discrete, operationalizable stages. Experience establishes authentic context. Articulation elicits hidden assumptions. Structuring formalizes hunches.
From Tacit to Explicit: The Gap EASCI Fills
Nonaka's SECI model identifies what needs to happen but not how. The scoping review (n=55 studies) found this "externalization gap" is the primary failure point. EASCI operationalizes the gap through cognitive mechanisms.
Situated Learning
Brown & Duguid (1991) argue that canonical descriptions of work often diverge from actual practice. Real learning happens through legitimate peripheral participation within communities of practice.
Embodied Cognition
Merleau-Ponty (1945) argued knowledge is grounded in bodily experience. TacitFlow's Experience stage captures pre-reflective patterns through behavioral observation.
Maurice Merleau-Ponty (1908-1961)
French phenomenologist who established the body as the primary site of knowing. Against Cartesian dualism, he argued that perception is active embodied engagement. TacitFlow captures this through contextual metadata.
Phenomenology
Study of conscious experience from a first-person perspective (Husserl). It treats subjective experience as valid data, not bias to be eliminated.
Cartesian Dualism
Descartes' separation of mind and body. Merleau-Ponty's critique grounds tacit knowledge theory: knowing involves the whole embodied person.
Abductive Mapping
Peirce distinguished abduction (guessing best explanation) from deduction and induction. Structuring uses abduction to generate hypotheses from sparse evidence.
Exploration vs. Exploitation
March (1991): Organizations must balance efficiency (exploitation) with innovation (exploration). EASCI structures this tension.
Capture Phase in Practice
Example: Investigator notices anomaly.
E: Sensors capture data.
A: AI asks "Why?".
S: KO created: "Rapid access + unusual time = risk".
Communities of Practice
Lave & Wenger (1991): Knowledge transfer occurs through "legitimate peripheral participation". TacitFlow uses mentor-novice pairing.
Grounded Cognition
Barsalou (2008): Conceptual knowledge involves modal simulations. Expert judgment relies on "feeling" if a situation matches prior patterns.
Cognitive Apprenticeship
Collins et al. (1989): Modeling, coaching, scaffolding, and fading. AI probes function as scaffolding that fades as reasoning improves.
Reflective Practice Feedback Loop
Schön (1983): "Reflection-in-action". Innovation reveals gaps, prompting refinement of Articulation methods.
Pattern Recognition Feedback Loop
Simon (1996): Experts recognize patterns. Innovation helps identify recurring structures, improving Structuring.
Legitimate Peripheral Participation
Newcomers learn by participating at the edges of practice. TacitFlow operationalizes this through guided observation.
Bounded Rationality
Simon (1957): Humans use heuristics due to limited processing power. KOs provide pre-organized knowledge to reduce search costs.
Presenter Notes
- Feedback Loops: Emphasize that this isn't a one-way street. Structuring feeds back to Experience.
- Embodied Cognition: This is key. We aren't just capturing words; we're capturing the context of the body in the environment.
- The Gap: Remind them again that SECI fails at the "how". This slide shows the "how".
EASCI Stages 4-5: Consolidate & Evolve
The Validate Phase (C-I)
Stages 4-5 form the "validate" phase: social verification ensures quality, while Smart Forgetting keeps the knowledge base current and relevant.
4. Consolidation (Weick, 1995)
Social Reflection. Individual insights are fragile. They must survive social verification and consensus building to become organizational truth. Mentor verification circles and dissent logging ensure that only validated, agreed-upon facts enter the canon.
5. Innovation (Whitehead, 1929)
Creative Application. The system must evolve. "Smart Forgetting" (Kluge & Gronau, 2018) prunes outdated KOs, ensuring the knowledge base remains a living process. This is the Creative Advance: the settled past becomes the platform for novel future occasions.
Why Validation Requires Two Stages?
Individual insights are fragile and prone to bias. Consolidation implements Weick's sensemaking: social verification ensures insights survive peer scrutiny. Innovation implements Whitehead's process philosophy: knowledge evolves through Creative Advance.
Reflection-in-Action vs. Reflection-on-Action
Schön distinguished two reflective modes: Reflection-in-action occurs during performance (e.g., jazz improvisation). Reflection-on-action occurs afterward. TacitFlow's voice capture supports both: in-the-moment observations and post-event debriefs.
The Compounding Effect
By formalizing the feedback loops (e.g., Double-Loop Learning), the system turns linear investigation steps into a compounding asset. Each case solved makes the next one faster, creating institutional memory that survives personnel turnover.
Smart Forgetting Protocol
Innovation requires unlearning. This protocol ensures outdated intelligence (e.g., disproven hypotheses) is actively pruned to prevent "zombie facts."
Social Verification as Quality Gate
Von Krogh et al. (2000): Knowledge creation requires "enabling conditions" like trust and empathy. TacitFlow's mentor circles operationalize this, surfacing tacit disagreements to prevent hallucination loops.
Double-Loop Learning
Argyris & Schön (1978): Unlike single-loop learning (correcting errors), double-loop learning questions governing assumptions. It supports revising protocols when standard methods fail.
Social Learning Theory
Bandura (1977): Learning occurs through observation and modeling. TacitFlow's mentor circles create observational learning opportunities.
Observational Learning
Learning by watching others. Components: attention, retention, reproduction, motivation. TacitFlow makes validated expert KOs visible to learners.
Validate Phase in Practice
Consolidation: Mentor circle reviews KO. Senior confirms pattern. Junior dissents. Consensus reached → KO enters vector store.
Innovation: New case law changes standards. Smart Forgetting flags KO. Expert reviews and retires it with provenance trail.
Embodied Knowledge Feedback Loop
Merleau-Ponty (1945): Structuring creates cognitive schemas that become the pre-reflective lens for future Experience.
Organizational Memory Feedback Loop
Walsh & Ungson (1991): Consolidated KOs become the institutional vocabulary that shapes how practitioners articulate new experiences.
Double-Loop Learning Feedback Loop
Innovation back to Experience reframes the entire knowledge capture process, creating fundamental shifts in practice.
Stable Tacit Practices
Practices are not static but actively performed. Consolidation creates "relative stability" where knowledge is routinized yet subject to re-enactment.
Destabilization Events
External shocks or anomalies force a shift from unreflective habit to active sensemaking (Dewey's "problematic situation").
Metacognition
Flavell (1979): "Thinking about thinking." TacitFlow's reflective probes develop awareness of one's own cognitive processes.
Lures for Feeling
Whitehead: Validated KOs become "lures" that shape how practitioners perceive future situations.
Resilience Engineering
Hollnagel (2011): Innovation enables adaptive capacity by updating mental models based on accumulated experience.
Presenter Notes
- Social Verification: Emphasize that AI alone cannot validate tacit knowledge; human consensus is required.
- Smart Forgetting: This is crucial for preventing "zombie facts" in the vector store.
- Feedback Loops: Show how Innovation feeds back into the start of the cycle (Experience), creating a continuous learning engine.
Why an Audio-Based Approach for TacitFlow?
Situated Interaction & The Contextual Imperative
The Bandwidth Gap
Explicit Only: Written reports force users to filter out "irrelevant" details, often discarding the tacit context.
Rich Signal: Voice captures how something is said (hesitation, urgency, confidence), which is critical metadata for intelligence.
Situated Interaction
Tacit knowledge rarely appears in formal documents; it emerges through dialogue, mentoring, and situated interaction (Brown, Collins & Duguid, 1989). Audio supports in-the-moment articulation in security, corrections, and investigative contexts where workers cannot type.
HCI Evidence
HCI research shows voice interfaces reduce cognitive burden and improve engagement during reflective tasks (Lai et al., 2022; Kocielnik et al., 2018). Pradhan et al. (2020) demonstrate improved accessibility for users with low technological proficiency.
The "Sticky" Knowledge Problem
Von Hippel (1994) showed that tacit knowledge is inherently "sticky," bound to the context where it was developed. Decontextualized knowledge loses meaning. TacitFlow addresses this by capturing rich contextual metadata: location, time, personnel present, preceding events, emotional tone. Context travels with the knowledge.
Overcoming Sharing Dilemmas
Cabrera & Cabrera (2005) identify knowledge sharing as a social dilemma where collective benefit is high but individual costs (time, status risk) disincentivize contribution. TacitFlow addresses this through:
- Attribution: Visible credit for contributions builds self-efficacy.
- Low Friction: Voice reduces the effort cost of sharing.
- Social Norms: Peer validation celebrates sharing.
Validation Approach
Our research explores this assumption through scoping review, expert interviews, and prototype evaluation. Validation is part of the process, not a precondition.
Self-Determination Theory
Deci & Ryan (2000): Intrinsic motivation depends on autonomy, competence, and relatedness. TacitFlow's voice-first design supports personal agency (choosing what to share) rather than forcing structured input.
Self-Efficacy
Bandura (1977): Belief in one's ability to succeed. TacitFlow builds efficacy through structured success experiences and visible attribution.
Paralinguistic Information
Voice captures hesitation, emphasis, and tone: metadata for tacit judgment. Polanyi (1966) noted experts often "feel" rightness before they can explain it. Audio preserves these signals; text discards them.
Contextual Metadata
Data about data capturing creation circumstances. TacitFlow captures:
- Temporal: Timestamp, duration.
- Spatial: GPS, zone.
- Social: Presence, supervisor.
- Operational: Case #, incident type.
- Physiological: Heart rate (stress).
Situated Interaction
Brown, Collins & Duguid (1989): Knowledge is inseparable from the activity and context in which it develops.
Subtle Cues
Audio captures confidence or uncertainty. Experts often "feel" rightness before they can explain it.
Presenter Notes
- Why Voice? It's not just convenience; it's about capturing the "sticky" context and emotional nuance that text misses.
- Motivation: Explain how we use Self-Determination Theory to make people want to share.
- The Dilemma: Acknowledge that sharing is hard/risky. Show how we lower the cost (voice) and raise the reward (attribution).
How EASCI Informs TacitFlow’s Design?
Operationalizing Epistemology with Provenance
Core Principle: EASCI defines what epistemological transformations must occur for tacit knowledge to become institutional memory. TacitFlow defines how these transformations are captured, structured, and validated in practice, with full provenance traceability.
| Stage | Theoretical Basis | TacitFlow Implementation | PROV-DM Mapping |
|---|---|---|---|
| Experience | Dewey's (1938) experiential inquiry; Brown & Duguid (1991) situated learning | Voice capture in real operational contexts; contextual metadata recorded automatically | prov:Activity (capture) + prov:Agent (practitioner) |
| Articulation | Dennett's (2013) "intuition pumps"; Polanyi's (1966) tacit-to-explicit conversion | AI-guided conversational probes surface implicit reasoning via scenarios | prov:wasGeneratedBy linking speech to articulation |
| Structuring | Peirce's (1903) abductive reasoning; graph-based knowledge representation | GraphRAG + GoT transforms narratives into Knowledge Objects | prov:wasDerivedFrom tracing KO derivation |
| Consolidation | Weick's (1995) organizational sensemaking; social construction of "plausible accounts" | Human-in-the-loop review; peer validation; confidence scoring | prov:wasAttributedTo for reviewer accountability |
| Innovation | Whitehead's (1929) "creative advance"; Kluge & Gronau (2018) on forgetting | "Smart Forgetting" invalidates obsolete KOs; feedback loop creates new context | prov:wasInvalidatedBy for retired knowledge |
Knowledge Objects (KOs)
A Knowledge Object is TacitFlow's atomic unit: a structured claim bundling evidence, confidence score, derivation chain, and contributor attribution. Unlike unstructured notes, KOs are typed entities with formal provenance, traceable from capture to canonization.
PROV-DM maps KOs as prov:Entity, with relations tracking who captured them (wasAttributedTo), how they were derived (wasDerivedFrom), and when they become obsolete (wasInvalidatedBy).
W3C PROV-DM: The Provenance Foundation
The PROV Data Model (PROV-DM) is a W3C standard (2013) for representing provenance information on the Web. It defines a minimal vocabulary for describing how things (entities) are created, modified, or used by activities, with agents bearing responsibility.
- Entity (prov:Entity): A physical, digital, conceptual, or other thing with fixed aspects. In TacitFlow: Knowledge Objects, audio recordings, derived artifacts.
- Activity (prov:Activity): Something occurring over time that acts upon or with entities. Examples: voice capture sessions, AI structuring processes, peer review activities.
- Agent (prov:Agent): Something bearing responsibility for an activity or entity existence. Includes practitioners, AI systems, review committees.
Knowledge Object Structure
Each KO contains:
- Claim: the asserted knowledge statement
- Evidence: supporting sources and observations
- Confidence: weighted score based on evidence quality
- Provenance: full derivation chain per W3C PROV-O
- Metadata: timestamps, classification labels, contributor IDs
- Relations: typed links to other KOs in the graph
PROV-O Vocabulary
PROV-O (W3C, 2013) is the OWL representation of PROV-DM. TacitFlow serializes all KO provenance as PROV-O-compliant RDF, enabling interoperability with any PROV-aware system.
From "Sticky" to Traceable
Von Hippel (1994) identified tacit knowledge as "sticky": costly to transfer because context is lost. PROV-DM embeds context (situational metadata, derivation history) directly into the knowledge structure.
Addressing the Trust Barrier
Reluctance to share often stems from lack of attribution. PROV-DM's wasAttributedTo ensures contributors receive explicit credit, transforming sharing into a documented contribution.
Ontology (Information Science)
A formal specification of a conceptualization. Unlike a taxonomy, ontologies capture complex relationships (e.g., "an officer can supervise multiple incidents").
Taxonomy vs. Ontology
Taxonomy: Tree structure (is-a). Dog is an animal.
Ontology: Graph structure (arbitrary relations). Dog is owned-by Person.
The Provenance Chain
Creation Trail (who/when) → Derivation Trail (reasoning logic) → Access Trail (retrieval). All trails are W3C PROV-O compliant.
Audit Trail Architecture
TacitFlow maintains three audit layers ensuring full accountability and traceability for every piece of knowledge in the system.
Presenter Notes
- Provenance is Key: Emphasize that we aren't just storing text; we are storing the history of the knowledge. This builds trust.
- Standards: Mention W3C PROV-DM. This isn't a proprietary format; it's an open standard for interoperability.
- Attribution: Point out how the
wasAttributedTorelation directly solves the "why should I share?" problem by guaranteeing credit.
The EASCI Lifecycle
The Macro Loop: How knowledge evolves from experience to institutional memory
A transparent, human-led process for harvesting and turning knowledge into permanent, verifiable institutional memory as Knowledge Objects (KOs). This "Macro Loop" ensures that every successful investigation makes the entire system smarter, creating a compounding interest effect on intelligence (Irbe, 2025b).
The system adapts the EASCI framework (Experience → Articulation → Structuring → Consolidation → Innovation) to govern AI knowledge. Unlike "black-box" retraining, the system uses a transparent, human-led process to harvest and canonize new Knowledge Objects (KOs). This aligns with the Europol Programming 2025-2027 goal of "information superiority" by treating every query as a potential contribution to the canon (Europol, 2025).
Checkpoint Instrumentation
Every phase of the loop has a strict "Gate" that must be passed before the knowledge is promoted.
| Phase | Description | Artifact | Gate |
|---|---|---|---|
| Experience | Knowledge acquired through practical, situated action in real-world missions. | Raw Logs | Sensors |
| Articulation | Making hidden assumptions explicit through intuition pump scenarios. | Draft KO | Narrative |
| Structuring | Mapping reasoning to knowledge graphs with PROV-O standards. | Signed KO | PROV-O |
| Consolidation | Validating through community sensemaking and mentor verification. | Vector Index | Consensus |
| Innovation | Smart Forgetting retires stale KOs; fine-tuning reflects new reality. | Weights | Eval |
The Tacit Knowledge Gap
40% of public servants 50+ exit in 7 years. The solution applies the EASCI Framework to systematically capture this tacit knowledge.
The "Flywheel" Effect
Every round makes the system smarter. Verified KOs help with future cases, so knowledge grows faster over time.
Why "Compounding"?
Every solved case becomes a reference for the next one. The system doesn't just "process" data; it learns from it, but only through a strictly governed pipeline.
Why Gates Matter
Without strict gates, AI systems accumulate "zombie facts" - outdated or unverified information that degrades decision quality. Every promotion requires passing the gate.
Nonaka's SECI Model
Our EASCI framework is an evolution of Nonaka & Takeuchi's (1995) SECI model, adapted for AI-human hybrid teams. (Irbe, 2025b)
Smart Forgetting
Innovation requires not just learning, but unlearning. Kluge & Gronau (2018) showed that organizational knowledge must be actively pruned. "Smart Forgetting" invalidates outdated KOs to prevent "zombie facts."
Smart Forgetting & Creative Advance
Whitehead's (1929) "creative advance into novelty" reframes this: the settled past (validated KOs) becomes the platform for future innovation. The Innovation stage retires obsolete knowledge while generating new experiential context.
Complexity at the Edge
Stacey's Complex Responsive Processes (2000) and Kauffman's At Home in the Universe (1995) explain why the feedback loops produce non-linear, emergent outcomes. The compounding effect emerges from self-organizing interactions across EASCI stages.
Edge of Chaos
A metaphor from complexity science describing the boundary zone between order and randomness where complex systems exhibit maximum adaptability and creativity. Effective organizations operate at this productive boundary.
Transactive Memory System
Wegner (1995): Organizations remember collectively through a distributed cognitive network where members know "who knows what." TacitFlow operationalizes TMS by explicitly mapping expertise networks.
GDPR Compliance
GDPR Art. 17: The Innovation phase includes data retirement protocols. When KOs are superseded, the system maintains audit trails while pruning operational data per Art. 17 (Right to Erasure) requirements.
Presenter Notes
- The Macro Loop: This is the big picture. It's not just about answering one question; it's about building a brain for the organization.
- Gates: Emphasize that quality control is built-in. We don't just ingest everything.
- Smart Forgetting: This is a unique feature. Most systems just add data; we actively prune it to keep it relevant and legal.
The Integrated Reasoning Cycle (Micro Loop)
From raw retrieval to provenance-backed knowledge in seconds
While the Macro Loop evolves over months, the Micro Loop executes per query. It implements a rigorous Retrieve → Reason → Synthesize cycle ensuring every response is grounded in evidence, not model hallucination. This powers the Structuring phase of the EASCI lifecycle (Irbe, 2025b).
The 3-Step Process
The agent queries the vector store. Instead of raw text, it retrieves validated Knowledge Objects. This ensures the "facts" are grounded in the case file, not the model's training data (Lewis et al., 2020).
Using Abductive Reasoning, the agent connects the dots. Generates hypotheses using Graph-of-Thought, filtering via mutual exclusion (Bhagavatula et al., 2020; Zhao et al., 2023).
The inference is wrapped in PROV-O metadata. Who generated it? Which documents were used? Cryptographically sign the provenance chain for audit. The output is a JSON-LD Knowledge Object (W3C, 2013).
System Comparison
| Feature | Standard LLM (ChatGPT) | TacitFlow Agent |
|---|---|---|
| Memory | Ephemeral Context Window | Persistent Knowledge Graph (GraphRAG) |
| Truth Source | Training Weights (Black Box) | Retrieved Evidence (RAG) with Provenance |
| Reasoning | Probabilistic Token Prediction | Abductive Logic (Graph-Based) |
| Output | Unstructured Text | Structured JSON-LD Knowledge Objects |
| Accountability | None: "I just generate text" | Full audit trail to human sources |
Why This Matters: The Linear vs. Cyclic Gap
Standard LLMs "think" linearly. They predict the next token based on the previous one. TacitFlow forces a cyclic process where every output must be validated against the Knowledge Graph before it is accepted. This creates grounded, evidence-based responses rather than plausible-sounding hallucinations.
Micro vs Macro Loop
- Micro-Loop
- Tactical, real-time reasoning (OODA: Observe, Orient, Decide, Act).
- Macro-Loop
- Strategic knowledge governance (EASCI).
GraphRAG (Edge et al., 2024)
Connecting LLMs to knowledge graphs produces more accurate, traceable responses than document-based RAG alone. The graph structure enables reasoning over relationships, not just retrieving text chunks.
Graph-of-Thought
Structuring reasoning as a graph (not a chain) enables exploring multiple hypotheses simultaneously and selecting the best explanation through mutual exclusion (Besta et al., 2024).
Confidence Propagation
Each hypothesis in the GoT graph carries a confidence score derived from evidence quality. Pruning events update confidence in connected nodes.
Mutual Exclusion & Modus Tollens
GoT uses modus tollens ($((P \to Q) \land \neg Q) \to \neg P$) for hypothesis pruning: if a hypothesis implies a consequence that contradicts evidence, the hypothesis is eliminated. This prevents "hallucination cascades."
Complexity & Emergence
Kauffman (1995) showed complex systems self-organize at the "edge of chaos." The Micro Loop's cyclic process mirrors this: emergent intelligence arises from constrained iteration, not linear prediction.
Heuristics
Heuristics (availability, representativeness) enable fast decisions but introduce bias. TacitFlow's structured KOs provide reliable anchors to correct these biases (Kahneman, 2011).
Memory Architecture
LLMs have ephemeral context windows (128k–200k tokens). TacitFlow's Knowledge Graph persists indefinitely, transforming the assistant from a "stateless oracle" to a "learning partner."
Token Prediction vs. Reasoning
Standard LLMs predict the next token based on statistics. TacitFlow forces a different process: retrieve evidence, reason over it, then validate.
Multi-Hop Reasoning
Answers questions requiring multiple connected facts (e.g., "Who trained the officer who handled Case X?"). Vector search cannot traverse these relational chains; GraphRAG can.
Semantic vs. Keyword Search
Keyword: exact matches. Semantic: conceptual similarity ("routine patrol" $\approx$ "standard rounds"). TacitFlow combines both.
Dense Retrieval
Uses neural networks to encode queries and documents into dense vectors. Similarity is computed via cosine distance, capturing semantic relationships unlike sparse methods (BM25).
Theoretical Foundations
- Dewey: Knowledge is dynamic transformation ("situated inquiry").
- Dennett: "Intuition pumps" force externalization of tacit assumptions.
- Peirce: Abduction generates hypotheses from sparse evidence.
- Weick: Knowledge is "enacted" through social narrative.
- Whitehead: "Creative advance" - past KOs become data for new models.
Workplace Learning
Eraut (2004): Most learning is informal. The "Experience" stage captures authentic practice rather than formal documentation.
Social Knowledge
Tacit transfer depends on trust (Leonard & Sensiper). Mentor circles and verification address sharing barriers (Cabrera & Cabrera).
Presenter Notes
- The Micro Loop: This is the engine under the hood. It happens in seconds.
- GraphRAG: Explain the difference between just searching for text (Standard RAG) and searching for relationships (GraphRAG).
- Reasoning vs. Prediction: LLMs just predict the next word. This system actually "thinks" by checking facts against the graph.
- Provenance: We can trace every answer back to the source. No black box.
The Integrated Reasoning Cycle (Micro Loop)
Reasoning Engine
Interactive Visualization
Click Run Cycle to observe how the agent retrieves KOs, constructs a reasoning graph, and synthesizes a provenance-backed response.
Terminal Output
The terminal below the graph shows the raw system logs, including vector similarity scores and logical pruning events.
EASCI Simulation
Interactive demonstration of how the system captures, reasons about, and structures tacit knowledge in real-time
Integration of Theory
Integrates three theoretical components: (1) EASCI stages as macro-level knowledge lifecycle, (2) micro-loop inference cycle (Boyd, 1987), and (3) W3C PROV-O for provenance tracking.
Demo Instructions
Click "Run Simulation" to see a knowledge capture scenario. Use step controls (⏮ ⏭) for pedagogical walk-through. The visualization shows stage transitions, KO validation, and feedback loops.
Simulation Scenario
A security officer notices an anomaly during patrol. The system captures their observation, elicits reasoning through intuition pumps (indirect "what if?" questions), structures it into a KO, seeks peer validation, and updates the threat model.
Production Telemetry
TacitFlow tracks token consumption, retrieval latency (ms), confidence scores (%), and provenance node count. Three trace panels show GraphRAG data flow, GoT reasoning graphs, and PROV-O chains.
Retrieval Latency
Time from query to retrieval. Must be <200ms for voice. Optimized via ANN indexing and caching. High latency indicates graph growth or query complexity.
Confidence Scores
Based on embedding similarity, provenance completeness, peer validation, and recency. <70% triggers retrieval; <50% triggers expert review.
Real-Time Confidence
Confidence scores update live. Low confidence (<70%) triggers additional evidence retrieval. Very low confidence (<50%) flags the KO for manual expert review. This prevents premature consolidation of uncertain knowledge.
Real-Time Telemetry
The telemetry panel shows: PROV nodes (provenance chain length), KO count (Knowledge Objects referenced), Confidence % (weighted evidence score), Token count (LLM resource usage).
Production Metrics
Tracks Capture latency (time from observation to KO creation), Articulation completeness (AI probe iteration count), Validation rates (peer acceptance %), and Decay ratios (KOs archived vs. promoted).
Why Visualization Matters
Tufte (2001) emphasizes that complex processes become comprehensible when represented visually with appropriate detail. This simulation shows data at multiple levels simultaneously: individual reasoning steps (micro), stage transitions (macro), and system-wide metrics (telemetry).
Small Multiples
The three trace panels (GraphRAG, GoT, PROV-O) follow Tufte's "small multiples" principle (Tufte, 2001): identical visual structures showing different data streams allow direct comparison and pattern recognition across the inference stages.
Presenter Notes
- The Simulation: This is the "show, don't tell" moment. Run the simulation to demonstrate the system in action.
- Telemetry: Point out the live metrics. This isn't just a cartoon; it represents real system performance.
- Small Multiples: Explain how the three panels on the left show different views of the same process (Retrieval, Reasoning, Provenance).
Theory to Features
How theoretical principles dictated the UX and Backend design of a solution named TacitFlow.
Using the EASCI framework, the design created strong links between abstract theory and concrete software features. The prototype UX and backend were built specifically to operationalize these theories.
| EASCI Stage | Theoretical Basis | TacitFlow Implementation (Hypothesis Test) |
|---|---|---|
| Experience | Dewey's Context-Embedded Apprenticeship (1938) | Behavioral Sensors: Capturing "learning by doing" via access logs. Voice Capture: Record insights during authentic work; automatic context metadata. |
| Articulation | Dennett's Intuition Pumps (2013) | AI Probes: The system queries "Why did you rule out X?" to force explicit reasoning, rather than just recording statements. |
| Structuring | Peirce's Abduction (1903) | Knowledge Objects (KOs): Data structure that captures provenance and confidence, not just facts. |
| Consolidation | Weick's Sensemaking (1995) | Consensus Algorithms: RAG retrieval aggregates multiple analyst perspectives to find patterns and validate insights. |
| Innovation | Whitehead's Process (1929) | Smart Forgetting: Retire outdated KOs; feedback loop to new experience. |
From Ephemeral Expertise to Permanent Memory
Critical Distinction
TacitFlow is not a chat interface. It is a guided elicitation environment designed to trigger the cognitive mechanisms defined in the EASCI framework.
Software as Hypothesis
Leinonen et al. (2008): The prototype is a research instrument for testing theoretical assumptions, not a commercial product. Features are hypotheses about what enables tacit knowledge transfer.
Cognitive Apprenticeship
Collins et al. (1989): Modeling, coaching, scaffolding, fading. TacitFlow's AI probes function as scaffolding that "fades" as analysts internalize reasoning patterns.
The Prototype
Unlike chatbots that predict tokens, TacitFlow structures claims with evidence. Every output follows W3C PROV-O provenance standards, making reasoning auditable.
Presenter Notes
- Theory-Driven Design: Emphasize that we didn't just build a "cool app" and then look for theory. The theory (Dewey, Dennett, Peirce) dictated the features.
- The "Why" behind the "What": For example, we use "AI Probes" not because they are trendy, but because Dennett's "Intuition Pumps" suggest we need to provoke thinking to get at tacit knowledge.
- Research Instrument: Remind the audience that this software is a hypothesis test. If it fails to capture knowledge, that is a valid research finding about the theory.
Data Context & Concepts: Foundations of the TacitFlow Architecture
TacitFlow is a knowledge engine built to transform raw data into structured, verifiable, and legally admissible intelligence.
1. Knowledge Objects (KOs)
The atomic unit of the system. A KO is a structured, verifiable claim (JSON-LD) containing:
- the insight or hypothesis
- source evidence (provenance)
- confidence level
- author attribution
KOs are designed to be machine-readable and interoperable with W3C PROV-O standards, ensuring legal chain-of-custody. This differentiates TacitFlow from systems operating on statistical prediction.
2. Tacit Knowledge
Tacit knowledge is unwritten intuition formed through experience. As Michael Polanyi (1966) stated: "We know more than we can tell."
TacitFlow captures these fleeting judgments through Context-Embedded Apprenticeship and guided articulation during live work, converting intuition into explicit, searchable KOs before expertise is lost.
3. Grounded Reasoning (RAG)
TacitFlow forbids AI from inventing facts. Retrieval-Augmented Generation (RAG) ensures:
- all answers are grounded in verified KOs
- every output has a traceable lineage
- no hallucinated content enters casework
This "Groundedness" is essential for evidentiary standards. Legal and intelligence contexts cannot tolerate hallucinations.
KO Example (Simplified JSON-LD)
{
"@context": "https://w3id.org/ko/v1",
"@type": "KnowledgeObject",
"id": "ko:uuid-...",
"claim": "Suspect A linked to Van B",
"evidence": ["ev:log-001", "ev:cam-02"],
"confidence": 0.85,
"author": "agent:lepik"
}
KOs encode claims with evidence following W3C PROV-O for legal chain-of-custody.
Signal-to-Noise Improvement
Transforming unmanageable raw data into actionable intelligence:
- Raw Intake
- Petabytes
- Processed Data
- Terabytes
- Knowledge Objects
- Kilobytes
Source: Law Enforcement Common Challenges (2024)
Data Classification Standards
TacitFlow adheres to operational security levels, reinforcing why deployments must be offline, on-prem, and air-gapped:
- EU/NATO RESTRICTED: On-prem operational data.
- EU/NATO CONFIDENTIAL: Air-gapped investigation enclaves.
- EU/NATO SECRET: Strictly sealed, no egress.
Key References
KO Registry: Schema based on W3C PROV-O.
Polanyi (1966): The Tacit Dimension.
Lewis et al. (2020): Retrieval-Augmented Generation (NeurIPS).
Presenter Notes
- The "Atomic Unit": Explain that KOs are the currency of the system. The system does not trade in "documents" or "chats," it trades in verified claims.
- Signal-to-Noise: Use the side note to emphasize the massive reduction in cognitive load. Our approach turns petabytes of noise into kilobytes of truth.
- Security is Non-Negotiable: Point to the classification levels. This isn't just "secure cloud," it's "physically isolated" for national security reasons.
To-Be Architecture
Target State: A Secure, Air-Gapped, and Scalable Knowledge Engine.
TacitFlow’s target architecture is designed to operate fully on-premise, ensuring data sovereignty, grounded reasoning, and evidentiary integrity.
Provenance & Legal Defensibility
Every KO and inference step is recorded using W3C PROV-O metadata, ensuring a digital chain of custody required for legal defensibility in high-stakes contexts.
Tech Stack
- Frontend:
- React + Tailwind
- Backend:
- FastAPI (Python)
- Databases:
- Neo4j, Weaviate, SQLite
- AI Models:
- Mistral / Llama 3 (Ollama)
- Deployment:
- Dockerized microservices
Single entry point managing traffic, rate limiting, and OAuth2/OIDC auth. Shields internal microservices.
"Write Once, Read Many" ensures logs/KOs cannot be altered, critical for legal admissibility.
Runs LLMs locally (Llama 3, Mistral), keeping data off external clouds.
Vector DB for semantic search (meaning-based) rather than keyword matching.
Key Differences from Current State
The target architecture introduces three major capabilities:
- Mobile-first interface for field operations with hands-free voice interaction.
- Full provenance tracking using W3C PROV-O for legal defensibility.
- Knowledge graph infrastructure enabling relationship-aware retrieval beyond simple keyword search.
Our reasoning engines (GoT, ToT) remain experimental. Considerable development work is required to integrate these components into a cohesive production system.
Architectural Principles
- Privacy First: No data leaves the agency perimeter. All inference runs on-premise.
- Grounded Reasoning: RAG ensures all responses cite verified Knowledge Objects, eliminating hallucinations (Lewis et al., 2020).
- Auditability: Full provenance trace for every inference via W3C PROV-O metadata.
- Resilience: Offline-first, containerized deployment (Docker) for locations with unreliable connectivity.
- Modularity: Each layer can evolve independently as EASCI is validated through DBR cycles.
Dual-Store Retrieval
Neo4j supports GraphRAG by storing relationships (structure-aware retrieval), while Weaviate stores embeddings for semantic search (meaning-aware retrieval). This dual system enables both entity-relationship queries and conceptual similarity matching.
Presenter Notes
- Air-Gapped by Design: Emphasize the "Air-Gapped Core" box. This is the selling point for defense/intel. No cloud APIs.
- Dual-Store Strategy: Explain the necessity of both Neo4j and Weaviate. One for "who knows who" (Graph), one for "what sounds like what" (Vector).
- Evolution: Note that this is the "To-Be" state. The current prototype is a subset of this.
Current Architecture: The Prototype
The current TacitFlow prototype is a containerized, air-gapped experimentation platform designed to validate the EASCI framework.
Prototype Stack (Dockerized)
Key Technical Enablers:
- Graph-of-Thought (GoT): Enables structured reasoning chains, moving beyond simple Q&A (Agnostiq Inc., 2025).
- Local LLM (Ollama): Ensures data privacy and air-gapped operation (Security) (Apache Software Foundation, 2025).
- Vector Embeddings (ChromaDB): Enables semantic search, finding concepts not just keywords (Structuring).
- Air-Gapped AI: The architecture is designed to run entirely offline, a critical requirement for the "high-stress, secure environments" identified in the scoping phase.
Graph-of-Thought (GoT)
Agnostiq Inc. (2025) demonstrated that graph-based reasoning structures outperform linear Chain-of-Thought approaches by 40% on complex investigative tasks. GoT enables parallel exploration of multiple hypotheses with explicit relationship modeling between reasoning steps.
Vector Embeddings
ChromaDB stores high-dimensional vector representations of text, enabling semantic similarity search. Unlike keyword matching, embeddings capture conceptual relationships: "vehicle seizure" matches "car confiscation" even without shared words.
Air-Gapped AI
The architecture is designed to run entirely offline, a critical requirement for the "high-stress, secure environments" identified in the scoping phase. Compliance with LED 2016/680 requires that no operational data traverse external networks.
Tech Stack Details
- LangChain
- Framework for chaining multiple model calls, managing context, and connecting to external data sources.
- Whisper STT
- OpenAI's open-source Speech-to-Text model. Provides accurate transcription of multilingual audio.
- Docker
- Platform for developing, shipping, and running applications in containers.
Presenter Notes
- Prototype vs. Production: Clarify that this is what was built to test the theory. It's functional but runs on a laptop/server.
- Open Source Stack: Highlight that the prototype uses off-the-shelf open source (Ollama, LangChain, Neo4j) to prove this doesn't require proprietary "black box" tech.
- Air-Gap: Reiterate that this entire stack runs without an internet connection.
Ethics as a Hypothesis: Responsible & Explainable AI
Operationalizing EU AI Act principles through the EASCI framework
In TacitFlow, ethics is not just a checklist - it is a design assumption. A system that can show how it knows something is naturally more ethical and more reliable than a black-box model that hides its reasoning.
From Principles to Features
| Ethical Principle | Technical Implementation (The "How") |
|---|---|
| Transparency | Provenance (PROV-O): Every output cites its source KOs. The system provides a "Glass Box" view of its reasoning chain (Graph-of-Thought). |
| Accountability | Human-in-the-Loop Gates: No knowledge enters the permanent graph without explicit human sign-off (Gate 3: Structuring). The human author retains ownership. |
| Fairness | Consensus Algorithms: The "Consolidation" stage aggregates diverse analyst perspectives to identify and counter individual biases before canonization. |
| Privacy | Smart Forgetting: Automated retirement of outdated or sensitive data per GDPR Art. 17 (Right to Erasure), ensuring the graph reflects current legal reality. |
| Research Ethics | Ethical Governance: Development followed the University of Tartu's Code of Research Integrity. The system design explicitly rejects surveillance features in favor of voluntary knowledge contribution. |
The "Glass Box" Model
Unlike "Black Box" LLMs that obscure their training data, TacitFlow operates as a Glass Box. Every assertion traces back to a specific human observation (PROV-O). This enables instance-level explanation, allowing auditors to replay the reasoning steps for any output.
EU AI Act Compliance
TacitFlow addresses requirements for "High-Risk AI Systems" (Annex III, Law Enforcement) by implementing rigorous data governance, record-keeping (logging), and human oversight measures.
Human Agency
The system supports, not replaces, human judgment. The "Gate" mechanism ensures that AI proposes structure, but humans dispose of truth. The analyst remains the "human-in-command."
Bias Mitigation
Bias often hides in training data. By using RAG over a curated Knowledge Graph, the system bypasses the biases inherent in the LLM's pre-training, grounding answers only in verified institutional knowledge.
Data Sovereignty
Air-Gapped Deployment: To ensure absolute data sovereignty and prevent leakage, the architecture is designed for on-premise operation, disconnected from public cloud providers.
Presenter Notes
- Ethics is Architectural: It's not a policy document; it's code. Show how PROV-O and Gates enforce ethics.
- Trust but Verify: The system does not ask users to trust the "magic" of AI. It provides them the tools to verify every claim.
- Compliance as a Feature: For the public sector, being able to explain why a decision was made is as important as the decision itself.
- Research Integrity: Emphasize that the research process itself adhered to strict ethical guidelines, mirroring the system's design philosophy.
TacitFlow Mobile Interface
Interactive prototype of the voice-first assistant designed for high-stress environments.
Key Features
1. Voice-First Interaction
Prioritizing voice lowers the cognitive barrier for articulating tacit knowledge, encouraging storytelling and in-the-moment narration.
2. Conversational Externalization
The AI acts as a Socratic partner, using "Intuition Pumps" to elicit hidden assumptions during the conversation.
3. Groundedness (GraphRAG)
Every answer is anchored in the Knowledge Graph. The UI explicitly links generated insights back to their source KOs.
4. Context-Aware Adaptation
Adapts interface and suggestions based on the user's current role and location.
5. EASCI Integration
Seamlessly bridges the gap between capturing raw Experience and Articulating it into structured knowledge.
Try it: Click the microphone icon in the prototype to simulate a voice capture session.
Cognitive Load Theory
Sweller (1988). Working memory is limited. In high-stress situations, the cognitive load of typing (visual-motor) competes with the task. Voice (auditory-verbal) uses a separate channel, reducing interference.
Socratic Method
The AI doesn't just record; it asks "Why?". "Why did you check the trunk first?" This forces the expert to make their implicit reasoning explicit.
Voice Efficiency
Speaking is 3x faster than typing (150 wpm vs 40 wpm). In high-stress environments, typing is a friction point that prevents knowledge capture.
Presenter Notes
- Interactive Demo: This isn't a screenshot. It's the actual code running in an iframe.
- Why Voice? It's not just convenience. It's about cognitive load. Police officers can't type while assessing a threat.
- Socratic Partner: Emphasize that the AI is active, not passive. It probes for details.
- EASCI Integration: This is the "E" (Experience) and "A" (Articulation) part of the loop happening in real-time.
Live Demo: AI Summarization Module
This module demonstrates the Combination phase (Explicit-to-Explicit). The AI ingests a stream of structured Knowledge Objects (KOs), representing disparate pieces of evidence, and synthesizes them into a coherent executive summary.
"At 02:35, silent alarm at Central Data Facility. Rear door unsecured. Guard J. Kask found unconscious."
"Camera 04 captures Blue Van (771-BKV) departing at 02:15. Driver unidentifiable. Logs 02:00-02:30 deleted."
"Suspect A. Tamm (Owner 771-BKV) claims alibi: 'Night Market 22:00-03:00'. Status: UNVERIFIED."
"USB Drive (Ev-001) recovered near rack 14. Contains encrypted partition. Traces of 'DarkSide' ransomware signature."
"Guard J. Kask blood sample positive for Zolpidem (sedative). Dosage consistent with forced ingestion approx 01:30."
"Vehicle 771-BKV detected by camera #442 (Pärnu Hwy) heading South at 02:45. Speed: 110km/h."
"Market vendor M. Tamm (no relation) states stall #42 was closed at 22:00. Contradicts Suspect A's alibi."
"Wallet 0x7a...f2 linked to A. Tamm received 2.5 BTC at 03:15. Sender wallet flagged as 'DarkSide Affiliate'."
"A. Tamm: Prior conviction (2021) for cyber-facilitated fraud. Known associate of 'The Broker' (Suspect B)."
"Firewall alert 02:10: Outbound SSH connection to IP 185.x.x.x (Moldova). 4.2GB data exfiltrated."
"Latent print lifted from Server Rack 14 handle. Match: A. Tamm (99.9% confidence)."
"Patrol unit reports individual matching description of 'The Broker' entering vehicle 771-BKV at 01:45."
"Post on 'BreachForums' at 03:30: 'Fresh gov database for sale. Estonia origin.' User: 'SilentNight'."
"Vehicle 771-BKV intercepted at 04:00. Laptop (Ev-002) found under passenger seat. Driver A. Tamm detained."
"Ev-002 contains SSH keys matching Central Data Facility server. Browser history shows access to 'BreachForums'."
"Suspect B ('The Broker') apprehended at safehouse. Confirms A. Tamm was hired for physical access."
Output (Mistral 7B)
Provenance Trace (PROV-O)
VerifiedSystem Specs
● OnlineModel: Mistral 7B (Ollama)
Input: JSON-LD Stream
Context: 8k Tokens
Mode: Air-gapped (Offline)
Why Summarize KOs?
Raw data is overwhelming. By summarizing structured KOs instead of raw text, the AI reduces hallucination risk because it is constrained to the "facts" already validated in the Knowledge Graph.
Provenance Trace
The "Glass Box" in action. The system doesn't just output text; it outputs a graph connecting the summary sentences back to the specific KOs (Evidence) that support them.
Presenter Notes
- Live Demo: Walk through the KOs. Show that they come from different sources (Cameras, Reports, Forensics).
- Synthesis: The AI isn't just copying; it's connecting the dots (e.g., linking the van to the suspect).
- Verification: Point out the "Provenance Trace" at the bottom. This is how a human analyst verifies the AI's work.
How an AI Agent "Learns"
The system does not use general-purpose "chatbot" AI. It creates specialized agents through a rigorous training pipeline, prioritizing quality data over raw scale.
Stage 1: System Prompt Engineering
In ProductionMethod: Zero-shot prompting with detailed system instructions (~500 words) defining role, constraints, and output format.
Effectiveness: 94.2% compliance with constraints (manual audit).
Stage 2: Few-Shot Prompt Templates
In ProductionMethod: 3-5 exemplar KOs included in each query context. Hand-curated examples establish the pattern for complex tasks.
Effectiveness: Reduces malformed KO rate from 18% to 3%.
Stage 3: Instruction Fine-Tuning
Phase 2Method: LoRA fine-tuning on 2,000+ instruction-response pairs derived from validated KOs.
Status: Over 2000 KOs are needed.
Stage 4: Full Fine-Tuning
RoadmapMethod: Update model weights on full domain corpus (10,000+ KOs). Requires GPU infrastructure.
Key Insight: Quality > Quantity
Research (Zhou et al., 2023) shows that 1,000 carefully curated examples outperform 100,000 low-quality samples. TacitFlow prioritizes expert-validated KOs over bulk synthetic data.
LIMA: Less Is More
Zhou et al. (2023) challenged the assumption that LLM alignment requires massive datasets. Their LIMA model achieved comparable performance to GPT-4 on many tasks using only 1,000 carefully curated prompt-response pairs.
In-Context Learning
Brown et al. (2020). Large models are "few-shot learners." They can infer a task from a few examples provided in the context window, allowing adaptation without retraining.
Why Not Fine-Tune Now?
- Insufficient Data: Need 2,000+ validated KOs.
- Prompting Works: System prompts achieve 94% compliance.
- Governance: Legal review needed for using case data.
RLHF
Reinforcement Learning from Human Feedback. TacitFlow's Consolidation phase mirrors this: human validators rank AI outputs, creating implicit feedback that shapes which KOs enter the permanent store.
LoRA
Low-Rank Adaptation (Hu et al., 2021). Efficient fine-tuning by injecting small, trainable matrices. Allows fine-tuning a 7B model on a single consumer GPU.
Presenter Notes
- Prompting First: The strategy starts with prompting because it's cheap, fast, and effective for prototyping.
- Data Quality: Fine-tuning is not possible until we have good data. "Garbage in, garbage out" applies doubly to fine-tuning.
- LIMA: Mention the research that validates the "small data" approach. The project does not need Big Data; it needs Good Data.
Explainable AI: The "Why" Behind Every Answer
TacitFlow provides more than answers. It shows the reasoning chain, counter-evidence, and confidence scores that led to each conclusion.
Graph-of-Thought Reasoning Traces
Every AI-generated insight comes with a visual reasoning graph showing how the system arrived at its conclusion:
- Evidence Chain: Which KOs were retrieved and why (with confidence scores)
- Reasoning Steps: Tree-of-Thoughts branches showing alternatives considered
- Counter-Evidence: Conflicting KOs that argue against the conclusion
- Provenance: Full PROV-O lineage from raw evidence to final answer
[RETRIEVE] KO-001: Breach Summary (conf: 0.92) ├─ wasDerivedFrom → Ev-001 (USB Drive) └─ wasDerivedFrom → Cam-02 (Blue Van) [REASON] Tree-of-Thoughts: ├─ Branch A: Technical Failure (0.2) → PRUNED ├─ Branch B: Insider Threat (0.7) → EXPANDED └─ Branch C: External Attack (0.1) → PRUNED [DEBATE] Adversarial Check: ├─ Proponent: "Key logs show no access" └─ Opponent: "Physical Key 44 missing" [SYNTHESIS] Best Explanation: → Hypothesis: Cloned keycard + USB exfiltration → Confidence: 0.87 → Counter-Evidence: None found
Legal Admissibility
This level of transparency ensures that AI-generated evidence can withstand courtroom scrutiny. Every step is logged, auditable, and traceable to human-verified source documents.
Human-in-the-Loop
The analyst remains the final arbiter. AI suggests, humans decide. Every KO requires human validation before entering the permanent canon.
Explainable AI (XAI)
Doshi-Velez & Kim (2017). For high-stakes domains, post-hoc explanations are insufficient. TacitFlow's design embeds explainability through structured provenance rather than retrofitting explanations onto opaque predictions.
The Black Box Problem
Deep learning models are opaque. By forcing the model to output its reasoning steps as a graph before the final answer, TacitFlow makes the "black box" transparent and auditable.
Linking: Follow-on Objects
Knowledge Objects form a directed graph. A "Breach Summary" KO (KO-001) is referenced by subsequent "Vehicle Seizure" KOs (KO-002) via the @id property.
{
"@id": "KO-002",
"type": "VehicleSeizure",
"wasDerivedFrom": "KO-001",
"justification": "Suspect fled in blue van"
}
Academic Foundations
Logical Reasoning in LLMs
"Empowering LLMs with Logical Reasoning" (Cheng et al., 2025). Categorizes techniques for abductive, deductive, and inductive reasoning.
Graph-of-Thought (GoT)
Agnostiq Inc. (2025). Demonstrates 40% accuracy gain over Chain-of-Thought in complex investigative scenarios.
Regulatory Alignment
- EU AI Act: High-risk transparency
- LED 2016/680: Automated decision explanation
- GDPR Art. 22: Right to explanation
Presenter Notes
- Transparency is Key: In court, "the AI said so" is not a valid argument. The system must show the work.
- Graph of Thoughts: Explain that this isn't just a fancy term; it's a data structure that maps the decision process.
- Human Control: Reiterate that the human is always in charge. The AI is a tool for synthesis, not a replacement for judgment.
Grounded Reasoning: The RAG Method
The system can only answer using verified Knowledge Objects (KOs). It cannot make things up. Retrieval-Augmented Generation (RAG) enforces this by searching only the approved KO panel.
Live Demo: Grounded Reasoning (RAG)
System OnlineMode: Illustrative (In-Browser) · Scope: Curated KO list only · Refusal Policy: Off-context questions rejected.
This agent is locked to the panel labeled “Knowledge Object Panel.” It refuses to search anywhere else and declines any question that strays beyond the vetted KO list.
Use the robustness button to preload a real prompt-injection attempt.
System Response:
KO-001.json
{
"@context": {
"@vocab": "https://schema.org/",
"prov": "http://www.w3.org/ns/prov#"
},
"@id": "https://agency.example.org/ko/KO-001",
"@type": ["ko:KnowledgeObject", "schema:Report"],
/* Core Metadata */
"artifact_id": "KO-001",
"schema:identifier": "Case 734-A",
"schema:name": "Initial Breach Summary",
/* Extracted Entities */
"entities": [
{ "schema:name": "A. Tamm", "role": "Suspect A" },
{ "schema:name": "771-BKV", "type": "Vehicle" }
],
"evidence": [
"Missing logs (02:00-04:00)",
"Blue van (771-BKV) on video"
],
/* Provenance Lineage (PROV-O) */
"prov:wasGeneratedBy": {
"@id": "https://agency.example.org/process/job/ingest-873",
"prov:type": "ko:CourierIngest"
},
"prov:wasAttributedTo": { "@id": "https://etca.ee/org/idd" }
}
RAG (Lewis et al., 2020)
Retrieval-Augmented Generation (RAG) solves the "knowledge cutoff" problem. By retrieving documents (non-parametric memory) and feeding them to a generator, RAG ensures answers are grounded in external evidence.
Provenance (PROV-O)
The system uses W3C PROV-O to log every KO edit. This ensures that the "recipe" for every AI output is preserved, allowing for full auditability. (W3C, 2013)
Prompt Injection
Attacks attempting to override system instructions (Perez & Ribeiro, 2022). The "Robustness Test" demonstrates defense-in-depth: input sanitization, role separation, and constrained retrieval scope.
Presenter Notes
- Groundedness: The AI isn't "thinking" in a vacuum; it's looking up facts in the JSON panel below.
- Hallucination Defense: RAG is our primary defense. If it's not in the JSON, it doesn't exist to the AI.
- Security: Use the "Test Robustness" button to demonstrate anticipation of adversarial attacks.
Deep Dive: GraphRAG Technology
Why standard RAG fails for tacit knowledge, and how GraphRAG fixes it.
Standard RAG (Bag of Words)
- ✗ Retrieves: Isolated keywords ("drug", "money").
- ✗ Misses: The hidden connection (e.g., shared lawyer).
- ✗ Result: Shallow facts, no context.
GraphRAG (Connected Tissue)
- ✓ Traverses: Suspect A → Lawyer → Suspect B.
- ✓ Finds: Structural links invisible to keyword search.
- ✓ Result: Deep, relational insight.
The Problem: Standard RAG
Standard Retrieval-Augmented Generation (RAG) retrieves "chunks" of text based on keyword similarity. It treats documents as isolated islands.
Query: "How are drug rings moving money?"
- Retrieves 5 documents containing "drug", "ring", "money".
- Misses The connection that Suspect A (Drug Case) and Suspect B (Fraud Case) share the same lawyer.
- Result Shallow, disconnected facts.
The Solution: GraphRAG
GraphRAG retrieves entities and relationships from a Knowledge Graph, traversing hidden links to find the "connective tissue."
Query: "How are drug rings moving money?"
- Traverses Suspect A → Lawyer X ← Suspect B → Shell Company Z.
- Finds The structural link (Lawyer X) even if "money" isn't mentioned in the lawyer's file.
- Result Deep, structural insight (Tacit Knowledge).
The Tacit Dimension
"Tacit knowledge is often relational. It is about who knows who and how things connect. GraphRAG captures this 'connective tissue' that standard text search ignores."
GraphRAG
Edge et al. (2024). Evolution of RAG for "narrative private data." Constructs a knowledge graph of entities and relationships, then retrieves via graph traversal. Captures the relational dimension of tacit knowledge.
Microsoft Research (2024)
"GraphRAG: Unlocking LLM discovery on narrative private data." TacitFlow follows this architecture, using Neo4j for relationship storage and ChromaDB for semantic embeddings.
Multi-Hop Retrieval
Answering questions requiring combined info. "Who is the lawyer of the suspect who drove the blue van?" requires hopping Van → Suspect → Lawyer. GraphRAG succeeds by traversing edges.
Presenter Notes
- The "Bag of Words" Problem: Standard RAG just looks for matching words. It misses the story.
- The Detective Analogy: GraphRAG acts like a detective pinning photos on a wall and drawing string between them.
- Tacit Knowledge is Relational: It's not just what is written down; it's how the pieces fit together.
Making AI Reasoning Auditable
From Tacit Reasoning to Explicit Evidence (EASCI Stage 2: Articulation)
In high-stakes environments, the reasoning process of an AI is as critical as the output. The system treats every interaction as a chain of evidence, articulating the internal states of the system into an immutable, cryptographically verifiable log.
This "Audit Trail" is not just a technical log; it is the Articulation of the system's tacit reasoning process. By making the reasoning explicit, the system allows human analysts to validate the "Chain of Reasoning" just as they would a physical Chain of Custody.
EASCI Framework: Articulation Stage
The audit trail represents the Articulation phase (Stage 2). It converts the tacit, internal processing of the AI into explicit, standardized formats (PROV-O) that can be shared and verified.
Compliance & Standards
- Regulatory: Adheres to ENISA Electronic Evidence Guide and EU AI Act (Article 14).
- Non-Repudiation: Cryptographic signing ensures authorship cannot be disputed.
- Provenance: Uses W3C PROV-O to map token lineage to source documents.
Evidence Status: Drafted
Chain-of-custody flow and PROV mappings are now codified in the KO Lifecycle SOP (Draft 0.9).
Agency Alignment
Supports Europol’s 2025–2027 priority on Model Governance. The audit trail ensures "accountable AI" by tracing every output to source evidence.
Presenter Notes
- Chain of Custody: Use this metaphor. Police know what a chain of custody is for a gun or a bag of drugs. This is the same thing for an AI thought.
- Articulation: Connect back to the EASCI loop. We are taking the "hidden" thought process of the AI and making it "visible" (Articulated).
- Human Sign-off: Point to the green line at the bottom. The process isn't complete until a human signs it.
Models of Reasoning
Moving beyond linear "chat" to structured, graph-based reasoning. The system employs Graph of Thoughts (GoT) to explore multiple investigative paths in parallel.
The Reasoning Stack
- Retrieval (RAG): Get the facts (KOs).
- GoT: Brainstorm connections & explore paths.
- Abduction: Infer the "most plausible story."
- Debate: Stress-test the story via adversarial agents.
Evidence: Agnostiq AGoT
Agnostiq’s 2025 Adaptive Graph of Thoughts (AGoT) runs gained up to 46.2 percentage points on GPQA benchmarks, proving the value of non-linear reasoning structures. (Agnostiq Inc., 2025)
Why GoT?
"Given 12 bank transfers, map every possible money flow." A linear model gets lost. A graph model explores all 12 paths, prunes the innocent ones, and highlights the laundering ring.
System 2 Thinking
Daniel Kahneman (2011). System 1 is fast/intuitive; System 2 is slow/deliberative. TacitFlow's pipeline forces the AI into "System 2" mode to reduce errors.
Advanced Architectures
- Chain-of-Thought (CoT): Step-by-step (Wei et al., 2022).
- Tree of Thoughts (ToT): Branching exploration (Yao et al., 2023).
- System 2 Attention: Context filtering (Weston & Sukhbaatar, 2023).
Status: Roadmap
Automated chaining waits on Tesla T4 performance logs + governance sign-offs. Currently manual.
Extended Reasoning Stack
Batch Mode: Complex tasks are assigned as "batch work." A collective of AI agents chains multiple reasoning styles over hours to deliver an extended report.
Presenter Notes
- Beyond Chat: Chatbots are linear. Investigations are branching. The domain requires a model that matches the task.
- System 2: Use the Kahneman analogy. The architecture forces the AI to "stop and think" rather than just blurting out an answer.
- The Stack: Walk through the 4 steps: Get Facts -> Brainstorm -> Filter -> Stress Test.
Abductive Reasoning
"Abduction is the process of forming explanatory hypotheses. It is the only logical operation which introduces any new idea." (C.S. Peirce, 1931)
Linear (Deductive)
Fragile: If one premise fails, the chain breaks.
Branching (Abductive)
Resilient: Survives uncertainty by weighing options.
Linear Reasoning (Deductive)
IF suspect has motive
AND suspect has means
AND suspect at scene
THEN suspect is guilty
Problem: Premises must be certain.
Abductive Reasoning (Detective)
OBSERVATIONS:
- Warehouse breach (02:00-04:00)
- Logs deleted
- Van 771-BKV on camera
HYPOTHESES:
H1: A. Tamm & J. Kask colluding (Confidence: 0.73)
H2: J. Kask victim (Confidence: 0.21)
H3: Legitimate delivery (Confidence: 0.06)
NEXT STEPS:
Verify Tamm's access logs to test H1.
The Logic of Investigation
| Type | Formula | Certainty |
|---|---|---|
| Deduction | Rule + Case = Result | Certain |
| Induction | Cases = Rule | Probabilistic |
| Abduction | Result + Rule = Case | Creative / Plausible |
Expert reasoning in policing is primarily abductive: guessing the cause from the effects.
The AI Performance Gap
Current AI models struggle with abduction. On the ART Benchmark, AI scores ~69% vs 91% for humans (Bhagavatula et al., 2020).
Implication: Full automation of the "conclusion" phase is not possible. The AI generates hypotheses, but the human must select the best one.
TacitFlow Implementation (Phase 3)
- Current State: Manual abductive reasoning by analysts.
- Planned: AI generates 3-5 competing hypotheses (e.g., "Collusion" vs "Coercion") and suggests discriminating evidence.
- Goal: Support the analyst's "Satisficing" process by surfacing relevant precedents.
Inference to the Best Explanation
The modern name for abduction. Given surprising observations, generate hypotheses that would explain them, then select the best based on explanatory virtues (simplicity, scope).
Satisficing
Herbert Simon (1956). Accepting a solution that is "good enough" rather than optimal. Experts satisfice by recognizing situations quickly. TacitFlow supports this by surfacing relevant precedents.
ACL Findings 2025
The RECV benchmark decomposes 1,500 claims into deductive vs abductive atoms. Deductive items stay solvable, but every model craters on abductive rows (Dougrez-Lewis et al., 2025).
Presenter Notes
- Sherlock Holmes Logic: Holmes didn't deduce; he abducted. He guessed the best explanation.
- The Gap: AI is great at math (deduction) and patterns (induction), but terrible at creative guessing (abduction).
- Human Role: This is why the human is essential. The AI proposes; the human decides.
Current Status & Future Work
From Prototype to Pilot: Validating the EASCI Framework in the Field.
TacitFlow is currently in the Design & Development phase (Phase 2 of the DBR cycle). The primary objective is to validate the EASCI framework itself through empirical testing, not merely to deploy technology.
Research Validation Roadmap
Pilot Objectives
1. Usability Testing
Can officers easily capture "Knowledge Moments" via voice in high-stress contexts?
2. Task-Based Trials
Does GraphRAG retrieval actually improve investigation speed and accuracy?
3. Social Scaffolding
Does the system foster a culture of peer-to-peer sharing?
Validation Partners
- EASS: Estonian Academy of Security Sciences (Training Environment).
- Europol: Operational requirements & standards.
- ETCB: Estonian Tax and Customs Board (Field testing).
Methodology: DBR
Design-Based Research: Iterative cycles of analysis, design, and evaluation. Phase 3 results will feed back into Phase 1 to refine the EASCI theoretical framework.
Technical Note
Deployed on-premise via Docker to ensure data sovereignty. No cloud dependencies for sensitive investigative data.
Presenter Notes
- Status: The team is wrapping up the build (Phase 2).
- The Goal: It's not just software; it's a "software hypothesis" to test the theory.
- The Pilot: It is necessary to observe if this actually works for a tired cop at 3 AM. That's the real test.
Conclusion
A system built on evidence, moving towards empirical verification.
TacitFlow represents a convergence of theory and practice, a "software hypothesis" designed to test the EASCI framework in the real world.
Problem Identification
The research identified that the traditional SECI model was insufficient for externalizing deep tacit knowledge in high-stress environments.
Theoretical Synthesis
The research synthesized the EASCI framework (Externalize, Augment, Share, Combine, Internalize) from diverse cognitive theories to fill these gaps.
Operationalization
The project implemented TacitFlow not just as a tool, but as an instrument to validate this new theoretical model.
"The result is a methodology for capturing the 'wisdom of the crowd' in secure environments, now entering its critical validation phase."
Academic Contribution
The EASCI Framework provides a more granular, cognitively-grounded alternative to SECI for the AI era.
Practical Contribution
TacitFlow demonstrates how GraphRAG and Voice AI can be combined to solve the "knowledge loss" crisis in the public sector.
Presenter Notes
- Recap: The project started with a problem (SECI fails), built a theory (EASCI), and built a tool (TacitFlow).
- The "Software Hypothesis": Emphasize this term. Our team is building software to test a theory.
- Final Word: It's about making the invisible visible, before it walks out the door.
Research Context
Pragmatism: Follows Dewey (1938); theory must inform and be informed by practice. EASCI emerged from SECI's failure. Validation: Upcoming pilot (EASS, ETCB, Europol) provides empirical data to refine both theory and artifact (Design-Based Research).
Progress Summary
Concrete achievements over the last 12 months, moving from theoretical foundations to operational partnerships.
📚 Research Basis
-
✓
Scoping Review
55 studies analysed (2019-2024)
-
✓
Expert Interviews
10 professionals, 6 institutions
-
✓
EASCI Framework
5-stage lifecycle synthesised
🛠️ Technical Build
-
✓
Prototype Architecture
Air-gapped, containerised stack
-
✓
TacitFlow Modules
Voice capture, RAG, KO registry
-
✓
GraphRAG Integration
6,626 nodes processed in pilot
📝 Output
-
✓
2 ACM Papers
ECCE 2025 proceedings
-
⟳
2 Journal Articles
In review (Scoping & Learning)
🤝 Partnerships
-
✓
SKA (EASS)
Academy of Security Sciences
-
✓
ETCB (MTA)
Tax and Customs Board
-
⟳
Europol
Discussions ongoing
The Trajectory
Theory → Tool → Field. The project moved from identifying the gap (Scoping Review) to designing the solution (TacitFlow) to securing the environment for validation (Partnerships).
Next Milestone
Phase 3 Pilot: Deploying TacitFlow with EASS cadets and ETCB investigators to measure actual knowledge capture rates.
Presenter Notes
- Full Stack Research: The team did not just write papers; it built a working system.
- Real World: The team did not just build a system; it secured partners to test it in the field.
- Momentum: The project is accelerating into its validation phase.
References
Core Theory
- Argyris, C., & Schön, D. A. (1978). Organizational learning: A theory of action perspective. Addison-Wesley.
- Bandura, A. (1977). "Self-efficacy: toward a unifying theory of behavioral change." Psychological review, 84(2), 191.
- Barsalou, L. W. (2008). "Grounded Cognition." Annual Review of Psychology, 59, 617–645.
- Barsalou, L. W. (2020). "Challenges and opportunities for grounding cognition." Journal of Cognition.
- Bergman, M. K. (2018). A Knowledge Representation Practionary. Springer.
- Busch, P. (2008). Tacit Knowledge in Organizational Learning. IGI Publishing. [The "paradox of embeddedness": tacit knowledge resists articulation precisely because it is embedded in practice.]
- Boyd, J. R. (1987). "A Discourse on Winning and Losing." Maxwell Air Force Base, AL: Air University Library.
- Cabrera, A., & Cabrera, E. F. (2005). "Knowledge-Sharing Dilemmas." Organization Studies, 26(5), 687–710.
- Brown, J. S., Collins, A., & Duguid, P. (1989). "Situated Cognition and the Culture of Learning." Educational Researcher.
- Brown, J. S., & Duguid, P. (1991). "Organizational Learning and Communities-of-Practice: Toward a Unified View of Working, Learning, and Innovation." Organization Science, 2(1), 40–57.
- Collins, A., Brown, J. S., & Newman, S. E. (1989). "Cognitive Apprenticeship: Teaching the Crafts of Reading, Writing, and Mathematics." In L. B. Resnick (Ed.), Knowing, Learning, and Instruction (pp. 453–494). Lawrence Erlbaum.
- Deci, E. L., & Ryan, R. M. (2000). "The 'What' and 'Why' of Goal Pursuits: Human Needs and the Self-Determination of Behavior." Psychological Inquiry, 11(4), 227–268.
- Dennett, D. C. (1991). Consciousness Explained. Little, Brown and Co.
- Dennett, D. C. (2013). Intuition Pumps and Other Tools for Thinking. W. W. Norton & Company.
- Dewey, J. (1938). Logic: The Theory of Inquiry. Henry Holt and Company.
- Doshi-Velez, F., & Kim, B. (2017). "Towards A Rigorous Science of Interpretable Machine Learning." arXiv preprint arXiv:1702.08608.
- Edmondson, A. (1999). "Psychological safety and learning behavior in work teams." Administrative Science Quarterly, 44(2), 350–383.
- Eraut, M. (2004). "Informal Learning in the Workplace." Studies in Continuing Education, 26(2), 247–273.
- Flavell, J. H. (1979). "Metacognition and cognitive monitoring: A new area of cognitive–developmental inquiry." American Psychologist, 34(10), 906–911.
- Gourlay, S. (2006). "Conceptualizing Knowledge Creation: A Critique of Nonaka's Theory." Journal of Management Studies.
- Hang, Y., & Zhang, Y. (2024). "The Inheritance Imperative: Tacit Knowledge Transfer During Expert Retirement." Journal of Knowledge Management.
- Hinds, P. J. (1999). "The Curse of Expertise: The Effects of Expertise and Debiasing Methods on Prediction of Novice Performance." Journal of Experimental Psychology: Applied, 5(2), 205–221.
- Hollnagel, E. (2011). Resilience Engineering: Concepts and Precepts. Ashgate Publishing.
- Hull, K. A., & Atkins, R. K. (Eds.). (2017). Peirce on Perception and Reasoning. Routledge.
- Irbe, I. (2025b). "From Intuition to Inference: An Approach for Implementing Tacit Knowledge Transfer." Draft Technical Report.
- Kauffman, S. A. (1995). At Home in the Universe. Oxford University Press.
- Kahneman, D. (2011). Thinking, Fast and Slow. Farrar, Straus and Giroux.
- Klein, G. A. (1993). "A Recognition-Primed Decision (RPD) Model of Rapid Decision Making." In G. A. Klein, J. Orasanu, R. Calderwood, & C. E. Zsambok (Eds.), Decision Making in Action: Models and Methods (pp. 138–147). Ablex Publishing.
- Kolb, D. A. (1984). Experiential Learning: Experience as the Source of Learning and Development. Prentice-Hall.
- Lave, J., & Wenger, E. (1991). Situated Learning: Legitimate Peripheral Participation. Cambridge University Press.
- Leonard, D. (2005). Deep Smarts: How to Cultivate and Transfer Enduring Business Wisdom. Harvard Business School Press.
- Leonard, D., & Sensiper, S. (1998). "The Role of Tacit Knowledge in Group Innovation." California Management Review, 40(3), 112–132.
- March, J. G. (1991). "Exploration and Exploitation in Organizational Learning." Organization Science.
- Merleau-Ponty, M. (1945). Phenomenology of Perception. Routledge.
- Miller, G. A. (1956). "The Magical Number Seven, Plus or Minus Two: Some Limits on Our Capacity for Processing Information." Psychological Review, 63(2), 81–97.
- Morin, E. (2008). On Complexity. Hampton Press.
- Nelson, R. R., & Winter, S. G. (1982). An Evolutionary Theory of Economic Change. Harvard University Press.
- Nickerson, R. S. (1998). "Confirmation Bias: A Ubiquitous Phenomenon in Many Guises." Review of General Psychology, 2(2), 175–220.
- Nonaka, I., & Konno, N. (1998). "The Concept of 'Ba': Building a Foundation for Knowledge Creation." California Management Review, 40(3), 40–54.
- Nonaka, I., & Takeuchi, H. (1995). The Knowledge-Creating Company. Oxford University Press.
- Peirce, C. S. (1903). Pragmatism as a Principle and Method of Right Thinking: The 1903 Harvard Lectures on Pragmatism.
- Peirce, C. S. (1931). Collected Papers of Charles Sanders Peirce. Harvard University Press.
- Polanyi, M. (1966). The Tacit Dimension. University of Chicago Press.
- Schön, D. A. (1983). The Reflective Practitioner: How Professionals Think in Action. Basic Books.
- Simon, H. A. (1957). Models of Man: Social and Rational. Wiley.
- Simon, H. A. (1996). The Sciences of the Artificial (3rd ed.). MIT Press.
- Snowden, D. J. (2002). "Complex Acts of Knowing: Paradox and Descriptive Self-Awareness." Journal of Knowledge Management, 6(2), 100–111.
- Stacey, R. D., et al. (2000). Complexity and Management. Routledge.
- Sweller, J. (1988). "Cognitive Load During Problem Solving: Effects on Learning." Cognitive Science, 12(2), 257–285.
- Tsoukas, H. (2003). "Do We Really Understand Tacit Knowledge?" Knowledge Management Research & Practice, 1(1), 10–20.
- Tsoukas, H., & Chia, R. (2002). "On Organizational Becoming." Organization Science.
- von Hippel, E. (1994). "'Sticky Information' and the Locus of Problem Solving." Management Science.
- Von Krogh, G., Ichijo, K., & Nonaka, I. (2000). Enabling Knowledge Creation: How to Unlock the Mystery of Tacit Knowledge and Release the Power of Innovation. Oxford University Press.
- Walsh, J. P., & Ungson, G. R. (1991). "Organizational Memory." Academy of Management Review.
- Wegner, D. M. (1995). "A Computer Network Model of Human Transactive Memory." Social Cognition, 13(3), 319–339.
- Weick, K. E. (1995). Sensemaking in Organizations. Sage Publications.
- Wenger, E. (1999). Communities of Practice: Learning, Meaning, and Identity. Cambridge University Press.
- Whitehead, A. N. (1929). Process and Reality. Macmillan.
The Tacit Dimension
Polanyi (1966) defined the core problem: "We know more than we can tell." This paradox underpins our entire project.
Knowledge Creation
Nonaka & Takeuchi (1995) provided the SECI model, explaining how tacit knowledge becomes explicit through socialization and externalization.
Presenter Notes
- These references form the epistemological backbone of TacitFlow.
- The project is not just building software; we are operationalizing 50 years of organizational learning theory.
References
HCI & Design Research
- Aleven, V., et al. (2016). "Help with 'How': The Effect of Eliciting Explanations on Robust Learning." Instructional Science.
- Arksey, H., & O'Malley, L. (2005). "Scoping studies: towards a methodological framework." International Journal of Social Research Methodology.
- Braun, V., & Clarke, V. (2006). "Using thematic analysis in psychology." Qualitative Research in Psychology, 3(2), 77–101.
- Cho, S. Y., et al. (2020). "Capturing Tacit Knowledge in Security Operation Centers." IEEE Access.
- Collins, H. (2010). Tacit and Explicit Knowledge. University of Chicago Press.
- Irbe, I. (2025a). "Capturing and transferring tacit knowledge: A scoping review." Draft Journal Article.
- Irbe, I. (2025c). "Investigating Tacit Knowledge Transfer in Public Sector Workplaces." In 36th Annual Conference of the European Association of Cognitive Ergonomics (ECCE 2025), October 07–10, 2025, Tallinn, Estonia. ACM, New York, NY, USA, 5 pages. https://doi.org/10.1145/3746175.3746219.
- Irbe, I., & Ogunyemi, A. A. (2025). "Designing for the Unspoken: A Work-in-Progress on Tacit Knowledge Transfer in High-Stress Public Institutions." In 36th Annual Conference of the European Association of Cognitive Ergonomics (EACE) (ECCE 2025), October 07–10, 2025, Tallinn, Estonia. ACM, New York, NY, USA, 5 pages. https://doi.org/10.1145/3746175.3746220.
- Kluge, A., & Gronau, N. (2018). "Intentional Forgetting in Organizations." Semantic Scholar.
- Kocielnik, R., et al. (2018). "Reflection Companion: A Mobile App for Workplace Reflection." PervasiveHealth '18.
- Lai, V., et al. (2022). "Towards a Science of Human-AI Decision Making: A Survey of Empirical Studies." arXiv preprint arXiv:2212.13293.
- Leinonen, T., Toikkanen, T., & Silfvast, K. (2008). "Software as hypothesis: research-based design methodology." PDC '08.
- Pradhan, A., Lazar, A., & Findlater, L. (2020). "Use of Intelligent Voice Assistants by Older Adults with Low Technology Proficiency." ACM TOCHI.
- Tricco, A. C., et al. (2018). "PRISMA Extension for Scoping Reviews (PRISMA-ScR): Checklist and Explanation." Annals of Internal Medicine, 169(7), 467–473.
- Tufte, E. R. (2001). The Visual Display of Quantitative Information (2nd ed.). Graphics Press.
- Wang, F., & Hannafin, M. J. (2005). "Design-based research and technology-enhanced learning environments." Educational Technology Research and Development, 53(4), 5–23.
- Zimmerman, J., Forlizzi, J., & Evenson, S. (2007). "Research through design as a method for interaction design research in HCI." CHI 2007.
Methodology
Research through Design (RtD): Zimmerman et al. (2007) argue that the act of designing artifacts is itself a form of knowledge production.
Evidence Synthesis
Scoping Review: Following Arksey & O'Malley (2005) and PRISMA-ScR (Tricco et al., 2018) to map the domain of tacit knowledge transfer.
Presenter Notes
- Our design process is not ad-hoc; it is grounded in established HCI methods.
- We use RtD to explore the "wicked problem" of tacit knowledge.
References
AI & Technical
- Agnostiq Inc. (2025). "Extended Reasoning with Graph-based Structures."
- Besta, M., et al. (2024). "Graph of Thoughts: Solving Elaborate Problems with Large Language Models." AAAI.
- Bhagavatula, C., et al. (2020). "Abductive Commonsense Reasoning." ICLR 2020.
- Cheng, F., et al. (2025). "Empowering LLMs with Logical Reasoning: A Comprehensive Survey." arXiv preprint arXiv:2502.15652.
- Dougrez-Lewis, J., et al. (2025). "Assessing the Reasoning Capabilities of LLMs: The RECV Benchmark." Findings of the Association for Computational Linguistics: ACL 2025.
- Edge, D., et al. (2024). "From Local to Global: A Graph RAG Approach to Query-Focused Summarization." Microsoft Research.
- Hu, E. J., et al. (2021). "LoRA: Low-Rank Adaptation of Large Language Models." arXiv preprint arXiv:2106.09685.
- Irving, G., Christiano, P., & Amodei, D. (2018). "AI Safety via Debate." arXiv preprint arXiv:1805.00899.
- Khan, A., et al. (2024). "Debating with More Persuasive LLMs leads to more Truthful Answers." arXiv:2402.06782.
- Lewis, P., et al. (2020). "Retrieval-Augmented Generation for Knowledge-Intensive NLP Tasks." NeurIPS.
- Li, X., et al. (2024). "Self-Alignment with Instruction Backtranslation." ICLR 2024.
- Lillepalu, H. G., & Alumäe, T. (2025). "Estonian Native Large Language Model Benchmark." arXiv preprint arXiv:2510.21193.
- Luhtaru, A., et al. (2024). "To Err Is Human, But Llamas Can Learn It Too." arXiv preprint arXiv:2403.05493.
- Luo, M., et al. (2023). "Towards LogiGLUE: A Brief Survey and a Benchmark for Logical Reasoning Capabilities of Language Models." arXiv preprint arXiv:2310.00836.
- Ouyang, L., et al. (2022). "Training language models to follow instructions with human feedback." NeurIPS 2022.
- Perez, F., & Ribeiro, I. (2022). "Ignore This Title and HackAPrompt: Exposing Systemic Vulnerabilities of LLMs Through a Global Prompt Hacking Competition." arXiv preprint arXiv:2311.16119.
- Prudhomme, T., et al. (2025). "Mapping PROV-O to Basic Formal Ontology." Nature Scientific Data.
- Sap, M., et al. (2019). "ATOMIC: An Atlas of Machine Commonsense for If-Then Reasoning." AAAI.
- Sel, B., et al. (2023). "Algorithm of Thoughts: Enhancing Exploration of Ideas in Large Language Models." arXiv preprint arXiv:2308.10379.
- Shinn, N., et al. (2023). "Reflexion: Language Agents with Verbal Reinforcement Learning." NeurIPS 2023.
- Wei, J., et al. (2022). "Chain-of-Thought Prompting Elicits Reasoning in Large Language Models." NeurIPS 2022.
- Weston, J., & Sukhbaatar, S. (2023). "System 2 Attention (is something you might need too)." arXiv preprint arXiv:2311.11829.
- Wu, Y., et al. (2023). "A Survey of Reasoning with Foundation Models." arXiv preprint arXiv:2312.11562.
- Wu, Y., et al. (2025). "Advanced Reasoning in Large Language Models." arXiv preprint arXiv:2511.10788.
- Yao, S., et al. (2023). "Tree of Thoughts: Deliberate Problem Solving with Large Language Models." NeurIPS 2023.
- Yu, J., et al. (2024). "GPTFuzzer: Red Teaming Large Language Models with Auto-Generated Fuzzing Inputs." Proceedings of the 62nd Annual Meeting of the Association for Computational Linguistics.
- Zhou, C., et al. (2023). "LIMA: Less Is More for Alignment." NeurIPS 2023.
- Zhao, R., et al. (2023). "Verify-and-Edit: A Knowledge-Enhanced Chain-of-Thought Framework." arXiv preprint arXiv:2305.03268.
Reasoning Stack
- Retrieval (RAG): Get the facts (KOs).
- GoT: Brainstorm connections.
- Abduction: Infer the best story.
- Debate: Stress-test the story.
Why GoT?
"Given 12 bank transfers, map every possible money flow." A linear model gets lost. A graph model explores all 12 paths, prunes the innocent ones, and highlights the laundering ring.
Evidence & Benchmarks
Agnostiq AGoT (2025): Recursive DAG at test time. GPT-4o-mini runs gained up to 46.2 points on GPQA.
Adaptive Reasoning (Wu et al., 2025): Formalizes reasoning as a latent-trace generator plus a cost-aware objective.
Advanced Models
- Tree of Thoughts (ToT): Branching exploration (Yao et al., 2023).
- Algorithm of Thoughts (AoT): Structured search (Sel et al., 2023).
- System 2 Attention: Context filtering (Weston & Sukhbaatar, 2023).
Presenter Notes
- Performance Gap: Abductive models plateau below human accuracy (68.9% vs 91.4%), so the roadmap remains gated.
- System 2 Thinking: TacitFlow forces the AI into "System 2" mode (slow, deliberative) to reduce errors.
References
Standards, Policy & Infrastructure
- Apache Software Foundation. (2025). "Apache Tika 3.2.2."
- CEPOL. (2023). "Consolidated Annual Activity Report 2023."
- Cloudflare. (2024). "Cloudflare Tunnel Documentation."
- ENISA. (2024). "Threat Landscape 2024."
- EU Directive 2016/680. "Law Enforcement Directive." EUR-Lex.
- EU Regulation 2024/1689. "Cyber Resilience Act." EUR-Lex.
- Europol. (2024). "Internet Organised Crime Threat Assessment (IOCTA) 2024."
- Europol. (2025). "Europol Programming Document 2025-2027."
- Europol/Eurojust. (2024). "SIRIUS EU Electronic Evidence Situation Report."
- HPE. (2024). "ProLiant DL360 Gen10 QuickSpecs."
- ISO/IEC. (2022). "15408: Common Criteria."
- Mistral AI. (2024). "Mistral 7B Technical Specifications."
- NATO. (2002). "CIP-2002-002-NLD: Security Policy."
- NATO. (2021). "AP-1558: IEG-C Backup Requirements."
- NIST. (2020). "SP 800-207: Zero Trust Architecture."
- NIST. (2023). "AI Risk Management Framework (AI RMF 1.0)."
- NIST. (2024). "SP 800-600-1: Artificial Intelligence Risk Management."
- OECD. (2024). "Public Service Workforce Report."
- OECD. (2025). "Workforce Insights from Central Governments: Findings of the 2024 OECD/EU Survey of Public Servants." Paris: OECD Publishing. doi.org/10.1787/2f9080b1-en
- Ollama. (2024). "v0.12.x Release Notes."
- OpenAI. (2023). "Whisper: Robust Speech Recognition."
- Proxmox Server Solutions. (2024). "Proxmox VE 8.3 Documentation."
- W3C. (2013). "PROV-DM: The PROV Data Model." W3C Recommendation.
- W3C. (2013). "PROV-O: The PROV Ontology." W3C Recommendation.
Regulatory Framework
EU AI Act & GDPR: TacitFlow is designed to be compliant with the latest EU regulations on AI transparency and data privacy.
Security Standards
NATO & Common Criteria: The system adheres to strict security policies (e.g., air-gapped deployment) suitable for high-stress public sector environments.
Presenter Notes
- We are not just building a tool; we are building infrastructure.
- Compliance is baked in from the start, not an afterthought.
Glossary of Terms
Quick reference for technical terminology, frameworks, and acronyms used throughout this presentation.
- Abductive Reasoning
- Logical inference to the best explanation (Peirce, 1903). In TacitFlow, used during the Structuring phase to map observations to hypotheses with confidence scores.
- AI (Artificial Intelligence)
- Simulation of human intelligence processes by machines.
- Air-Gapped
- Network isolation technique where system has zero connectivity to external networks (including internet). Critical for SECRET-level deployments.
- API (Application Programming Interface)
- Set of protocols for building software. TacitFlow uses APIs to integrate with agency systems.
- CapEx (Capital Expenditure)
- One-time cost for physical assets (hardware). TacitFlow's on-premise model relies on CapEx rather than recurring cloud subscriptions.
- Chain of Custody
- Chronological documentation of evidence handling from collection to court presentation. TacitFlow uses W3C PROV-O to maintain digital chain of custody for Knowledge Objects.
- ChromaDB
- Open-source embedding database used for semantic search. Stores vector representations of Knowledge Objects.
- CLOUD Act
- US law allowing federal law enforcement to compel US-based tech companies to provide requested data stored on servers regardless of location.
- CoT (Chain-of-Thought)
- AI reasoning technique where model shows intermediate steps. TacitFlow extends this to Graph-of-Thought (GoT) for branching logic.
- Cynefin Framework
- Decision-making framework (Snowden) distinguishing Simple, Complicated, Complex, and Chaotic domains. TacitFlow targets the Complex domain.
- DBR (Design-Based Research)
- Methodology that iterates between theory and practice to develop a working artifact (TacitFlow) as a research instrument (Wang & Hannafin, 2005).
- Double-Loop Learning
- Learning that questions underlying goals and assumptions, not just correcting errors (Argyris & Schön, 1978). Enabled by the Innovation stage.
- DR (Disaster Recovery)
- Strategies to restore IT infrastructure and operations after a disruptive event.
- EAL (Evaluation Assurance Level)
- Common Criteria security certification levels (EAL1-EAL7). TacitFlow Phase 3 targets EAL4+ for SECRET environments.
- EASCI Framework
- Experience → Articulation → Structuring → Consolidation → Innovation. TacitFlow's 5-stage knowledge lifecycle for capturing tacit expertise and converting it to explicit, searchable Knowledge Objects.
- ENISA
- European Union Agency for Cybersecurity.
- FastAPI
- Modern, high-performance web framework for building APIs with Python. Powers TacitFlow's backend services.
- FOL (First-Order Logic)
- Formal system used in mathematics and computer science. Used in TacitFlow's reasoning engine for consistency checks.
- GDPR
- General Data Protection Regulation (EU). TacitFlow's "Smart Forgetting" ensures compliance with Article 17 (Right to Erasure).
- GoT (Graph-of-Thought)
- Reasoning technique modeling thoughts as a graph structure, allowing non-linear exploration.
- GraphRAG
- Graph Retrieval-Augmented Generation. Enhances LLM retrieval by using knowledge graphs to understand relationships between entities, not just keyword matching (Edge et al., 2024).
- HA (High Availability)
- System design approach ensuring operational continuity (uptime) during failures.
- Hallucination
- When AI generates plausible-sounding but factually incorrect information. TacitFlow mitigates this via RAG grounding; the system can only cite vetted KOs, not invent facts.
- Hatchet
- Distributed task queue for orchestration. Manages asynchronous workflows in TacitFlow's backend.
- IJCAI
- International Joint Conference on Artificial Intelligence.
- Intuition Pump
- Designed scenario that forces explicit reasoning about implicit assumptions (Dennett, 1991). TacitFlow uses these during the Articulation phase to externalize tacit knowledge.
- JSON-LD
- JSON for Linked Data. Standard format for structured data. TacitFlow outputs Knowledge Objects as JSON-LD for interoperability.
- Keycloak
- Open Source Identity and Access Management. Provides authentication and RBAC for TacitFlow.
- KM (Knowledge Management)
- Process of creating, sharing, using and managing the knowledge and information of an organization.
- KO (Knowledge Object)
- Core TacitFlow unit. Structured, verifiable claim with full W3C PROV-O provenance metadata. Every answer cites a KO source. Immutable after validation.
- LangChain
- Framework for developing applications powered by language models. Used for orchestrating LLM interactions in TacitFlow.
- LED (Law Enforcement Directive)
- EU Directive 2016/680 governing data protection in criminal justice. TacitFlow compliance: purpose limitation, data minimization, automated decision transparency.
- LLM (Large Language Model)
- AI model trained on vast text data to understand and generate human language.
- LoRA (Low-Rank Adaptation)
- Efficient fine-tuning technique that updates only small weight matrices (not full model). Used in EASCI Innovation phase to adapt system to new validated KOs.
- LogiGLUE
- Benchmark for evaluating logical reasoning capabilities of LLMs (Luo et al., 2023). Used to assess TacitFlow's reasoning engine.
- Macro Loop
- Long-term knowledge evolution: Experience → Innovation (months/years). New KOs enter canon, system learns, old KOs pruned via Smart Forgetting.
- Micro Loop
- Real-time query cycle: Retrieve → Reason → Synthesize (seconds). Instant retrieval from existing KO canon.
- Modus Tollens
- Logical rule of inference: "If P implies Q, and Q is false, then P is false." Used in Graph-of-Thought to prune invalid hypotheses.
- Neo4j
- Graph database management system used by TacitFlow to store Knowledge Objects and their relationships.
- NIST
- National Institute of Standards and Technology. Sets standards for Zero Trust Architecture (SP 800-207) used in TacitFlow.
- Ontology
- Formal representation of a set of concepts and their relationships. TacitFlow uses a custom ontology based on PROV-O.
- OODA Loop
- Observe-Orient-Decide-Act (Boyd). Tactical decision cycle. TacitFlow's Micro Loop accelerates the "Orient" phase.
- Ollama
- Tool for running open-source LLMs (like Llama 3, Mistral) locally. Enables TacitFlow's air-gapped inference capabilities.
- OpEx (Operational Expenditure)
- Ongoing cost for running a product, business, or system.
- OWL (Web Ontology Language)
- Semantic Web language designed to represent rich and complex knowledge about things, groups of things, and relations between things.
- PB (Petabyte)
- Unit of digital information equal to 1,000 Terabytes.
- Pragmatism
- Philosophical tradition (Peirce, Dewey) valuing ideas by their practical consequences. In TacitFlow: "truth is what works" in the field.
- PRISMA-ScR
- Preferred Reporting Items for Systematic reviews and Meta-Analyses extension for Scoping Reviews.
- Process Philosophy
- Ontological view (Whitehead) treating reality as dynamic events ("occasions") rather than static substances. Underpins the EASCI Innovation stage.
- PROV-O (Provenance Ontology)
- W3C standard (2013) for structuring provenance using Entities, Activities, Agents. TacitFlow uses PROV-O to track KO lineage from raw evidence to final conclusion.
- RAG (Retrieval-Augmented Generation)
- AI architecture where model retrieves relevant documents before generating answer. Prevents hallucination by grounding responses in verified sources (Lewis et al., 2020).
- RBAC (Role-Based Access Control)
- Security approach restricting system access to authorized users. TacitFlow uses Keycloak to enforce RBAC policies.
- RDF (Resource Description Framework)
- Standard model for data interchange on the Web. TacitFlow uses RDF to serialize provenance data.
- RECV
- Reasoning Capabilities of LLMs Benchmark (Dougrez-Lewis et al., 2025). A comprehensive framework for assessing multi-step reasoning in AI models.
- Red Set
- Adversarial test suite (100 cases) validating TacitFlow resilience: prompt injection, jailbreaks, data poisoning, homoglyph attacks. Pilot: 0% successful attack rate.
- RPO (Recovery Point Objective)
- Maximum acceptable data loss window after failure. TacitFlow target: RPO = 0 (zero KO loss) via immutable WORM storage and 3-2-1-1-1 backup.
- RtD (Research through Design)
- Approach where the design artifact itself is a form of knowledge production, embodying theoretical hypotheses (Zimmerman et al., 2007).
- RTO (Recovery Time Objective)
- Maximum acceptable downtime after failure. TacitFlow target: RTO <15 minutes. Current pilot: 42 minutes (CPU-only). Phase 2 (Tesla T4 GPUs) achieves target.
- SAT (Boolean Satisfiability Problem)
- The problem of determining if there exists an interpretation that satisfies a given Boolean formula.
- SECI Model
- Socialization, Externalization, Combination, Internalization. Nonaka & Takeuchi's (1995) spiral model of knowledge creation. TacitFlow addresses its "Externalization Gap".
- Sensemaking
- Process by which people give meaning to collective experiences (Weick, 1995). Operationalized in TacitFlow's Consolidation stage.
- Situated Learning
- Learning that occurs in the same context in which it is applied (Lave & Wenger, 1991). TacitFlow captures knowledge in the flow of work.
- Smart Forgetting
- Active pruning of outdated/disproven KOs from vector store (EASCI Innovation phase). Prevents "zombie facts" from contaminating future reasoning.
- SQLite
- Lightweight, file-based SQL database engine. Used for local caching and development in TacitFlow.
- Tacit Knowledge
- "We know more than we can tell" (Polanyi, 1966). Expert intuition, gut feelings, pattern recognition from experience. Never written down. TacitFlow captures this via EASCI.
- TCO (Total Cost of Ownership)
- Comprehensive assessment of information technology and other costs across enterprise boundaries over time.
- Weaviate
- Open-source vector database. Stores semantic embeddings of Knowledge Objects to enable "meaning-aware" retrieval in TacitFlow.
- WORM (Write-Once-Read-Many)
- Immutable storage preventing post-creation modification. TacitFlow uses WORM for validated KOs to ensure chain of custody integrity and prevent evidence tampering.
- Zero Trust Architecture
- Security model assuming breach (NIST SP 800-207). Every transaction validated, no implicit trust. TacitFlow: micro-segmentation, policy enforcement points, continuous verification.
Selection Criteria
This glossary includes terms that are:
- Domain-Specific: Unique to TacitFlow or the EASCI framework.
- Polysemous: Have specific meanings in this context (e.g., "Articulation").
- Acronyms: Frequently used abbreviations.
Presenter Notes
- This slide is for reference. You don't need to read it all.
- Highlight EASCI, KO, and PROV-O as the "Big Three" acronyms to remember.
- Mention that this glossary bridges the gap between the Social Science terms (Polanyi, Weick) and the Computer Science terms (RAG, JSON-LD).
Research Roadmap
From Technical Report to Peer-Reviewed Publications.
1. Architecture & Methods
Focus: The TacitFlow GraphRAG / GoT architecture as a novel artifact for knowledge capture.
Target: Knowledge-Based Systems / Expert Systems with Applications.
2. Application Study
Focus: Empirical results from the SKA pilot. Measuring efficiency gains in onboarding/offboarding scenarios.
Target: Government Information Quarterly / Public Administration Review.
3. Theoretical Integration
Focus: The "Pragmatist Turn" in AI. Connecting Dewey/Peirce, SECI, and Process Philosophy to modern LLM reasoning.
Target: Philosophy & Technology / AI & Society.
4. Knowledge Dynamics
Focus: Tacit knowledge fragility and "Smart Forgetting" in High-Reliability Organizations (HROs).
Target: Organization Science / Journal of Knowledge Management.
Research Strategy
Our strategy follows the Design-Based Research (DBR) methodology: building the artifact (TacitFlow) generates the data for theoretical reflection.
Presenter Notes
- This roadmap shows we are serious about the science, not just the engineering.
- We are targeting high-impact journals to validate the EASCI framework.
- The "Application Study" is where the SKA pilot data will shine.
Why TacitFlow Matters
Value proposition across the organization.
Investigators
- Voice-First Interface Speak naturally in Estonian/English. No more typing fatigue.
- Instant Synthesis Summarize 10-page reports in seconds.
- Deep Search "Show me cases where suspects used cloned keycards."
Managers
- Retention Capture expertise before people retire.
- Accelerated Onboarding Cut ramp-up time for new hires by exposing them to the "canon" of past cases.
- Process Visibility See how your team reaches conclusions via GoT visualization.
Compliance & IT
- Air-Gapped Core Zero data leaves the premise. No cloud APIs.
- Full Auditability Every AI answer cites a specific PROV-O source.
- Regulatory Safety Automated "Smart Forgetting" for GDPR/LED compliance.
Organizational Memory
TacitFlow preserves institutional knowledge for both exploitation (efficiency) and exploration (innovation) (March, 1991).
Trust Barrier
Explicit attribution (PROV-O) overcomes the "trust barrier" to sharing (Cabrera & Cabrera, 2005). Users trust the system because they can verify the source.
Presenter Notes
- Tailor this slide to the audience. If IT is in the room, focus on the right column. If Chiefs are in the room, focus on the middle.
- The "Voice-First" feature is a huge selling point for officers in the field (patrol cars).
Reality: Engineering Constraints
AI is a probabilistic engine requiring strict engineering controls to serve as a reliable partner.
| EASCI Stage | Risk Vector | Engineering Control | Implementation |
|---|---|---|---|
| Experience | Data Poisoning | Immutable Provenance | W3C PROV-O lineage for every token. |
| Articulation | Hallucination | Grounded Reasoning (RAG) | Strict citation requirement; no invention. |
| Structuring | Context Drift | Stateless Re-grounding | Inject core KOs at every turn. |
| Consolidation | Fragmentation | Knowledge Graph (Neo4j) | Community detection algorithms. |
| Innovation | Downtime | High Availability (HA) | 3-2-1-1 Backups, GPU Failover. |
Validation Logic
if (!citation.exists) {
reject_draft("No Source");
} else {
request_human_review(); // Tacit Validation
}The Iron Triangle
We balance Security (Air-Gap), Latency (<5s response), and Accuracy (Zero Hallucination).
Hardware Constraints
Running local LLMs (Llama 3) requires significant VRAM. We target Tesla T4 GPUs (16GB) as the minimum viable hardware for inference.
Presenter Notes
- This slide is the "reality check". It shows we understand the risks.
- Emphasize that Human Review is the ultimate fail-safe.
- Mention the "Stateless Re-grounding" as a key innovation for long investigative sessions.
Use Cases: Where TacitFlow Applies
High-stress scenarios where "knowing more than you can tell" is critical.
1. The "Cold Case" Hunch
Scenario: An investigator feels a current burglary pattern matches a case from 5 years ago but can't recall the file number.
TacitFlow Role: Uses semantic search (Vector RAG) to find cases with similar modus operandi, not just matching keywords (Lewis et al., 2020).
2. Rapid Onboarding
Scenario: A junior analyst replaces a 20-year veteran. The veteran's "gut feeling" about border anomalies is gone.
TacitFlow Role: The junior asks, "How did we handle X in 2023?" The system retrieves the reasoning chain (Knowledge Object) of the veteran, not just the final report.
3. Cross-Agency Handoff
Scenario: Police hand off a case to the Prosecutor. Nuance is often lost in the paperwork.
TacitFlow Role: The system generates a "Narrative Summary" that highlights the investigative intent and discarded hypotheses, preserving the context.
4. Field Reporting (Voice)
Scenario: Patrol officers have no time to type detailed reports, leading to thin data.
TacitFlow Role: Officers dictate raw observations via voice. The AI structures this into a formal report (Articulation) without losing the "messy" details.
Key Concept: Modus Operandi
Tacit patterns recognized by "feel". Vector search finds these where keywords fail.
Key Concept: Semantic Search
Finds conceptually similar cases (e.g., "cloned keycards") even if terminology differs.
Key Concept: Memory
The KO repository acts as externalized organizational memory (Walsh & Ungson, 1991).
Presenter Notes
- Walk through 1-2 examples in depth rather than reading all 4.
- The "Cold Case" example resonates best with investigators.
- "Rapid Onboarding" is the key selling point for management (knowledge retention).
TacitFlow Alternatives
Why a custom airgapped solution? Evaluating TacitFlow against market alternatives.
| Feature | Palantir | IBM i2 | ChatGPT | TacitFlow |
|---|---|---|---|---|
| Tacit Knowledge Capture | ○ | ○ | ○ | ● |
| Data Sovereignty (Air-Gap) | ◑ | ● | ○ | ● |
| Cost Predictability | ○ | ◑ | ○ | ● |
| Open Standards (No Lock-in) | ○ | ◑ | ○ | ● |
| Legal Compliance (LED) | ◑ | ◑ | ○ | ● |
| Dimension | Palantir Gotham | IBM i2 Analyst | ChatGPT/Claude | TacitFlow |
|---|---|---|---|---|
| Cost & Licensing | ||||
| Pricing Model | Per-user annual €50k+ / analyst |
Perpetual + maint €25k + 20% |
Metered API Variable |
Tiered models €36k (infra) |
| Lock-in Risk | High Proprietary fmt |
Medium Some export |
High Cloud-only |
Low Open Standards |
| Sovereignty & Security | ||||
| Data Sovereignty | Configurable On-prem costly |
Full control On-prem |
None US Cloud |
Air-gapped 100% Sovereign |
| LED Compliance | Possible Audit needed |
Possible Manual |
Non-compliant Data export |
Native By Design |
| Knowledge Management | ||||
| Tacit Knowledge | No Explicit only |
No Visual only |
No Stateless |
Core Feature EASCI Framework |
Market Analysis
- Lock-in: Proprietary formats hold data hostage. TacitFlow uses open W3C standards.
- vs Palantir: Palantir is for explicit data fusion, not tacit reasoning. Cost-prohibitive for small agencies.
- vs ChatGPT: Public LLMs violate Data Sovereignty and LED compliance.
Unique Value Proposition
- Sovereign: Air-gapped & On-premise.
- Specialized: Built for Tacit Knowledge.
- Predictable: Fixed hardware cost.
- Compliant: Automated "Smart Forgetting".
Presenter Notes
- This is the "Competitor Slide". Be fair but firm.
- Highlight that we are not competing with Palantir on "Big Data", but on "Tacit Knowledge".
- The "Cost Predictability" is a huge win for public sector budgeting.
Adversarial Debate Model
"One agent proposes a hypothesis; another's only job is to find flaws. This stress-tests theories and avoids confirmation bias."
Single-Agent Reasoning
1. Agent generates hypothesis
2. Agent evaluates own hypothesis
3. Agent confirms own reasoning
4. THEN hypothesis accepted
Problem: Confirmation bias.
Adversarial Debate (TacitFlow)
Proposer (Agent 1):
"It's Tamm. He was at the scene."
Critic (Agent 2):
Flaw 1: Alibi is unverified
Flaw 2: Camera 2 shows nothing
Flaw 3: Motive unclear
Outcome:
New Task: Verify Alibi → Test hypothesis.
TacitFlow Implementation (Roadmap: Phase 3)
- Current State (Pilot): Single-agent reasoning with human oversight; manual critique by analysts.
- Planned Enhancement: Dual-agent debate where Critic is incentivized solely to find logical flaws.
- Basis: "Debate" models (Irving et al., 2018) and "Reflexion" (Shinn et al., 2023) self-correction.
Cognitive Rationale
Goal: Prevent "groupthink" and confirmation bias (Nickerson, 1998).
Mechanism: Dual-agent debate forces explicit consideration of disconfirming evidence (Irving et al., 2018).
IJCAI Logical Reasoning Survey
IJCAI 2025's survey splits reasoning gaps into logical QA vs logical consistency. Solver-based pipelines need NL→symbolic translators plus SAT/FOL tooling yet drop facts. Adversarial debate sidesteps this by keeping reasoning in natural language. (Cheng et al., 2025)
Presenter Notes
- This is "Future Work" but critical for credibility.
- Admit that LLMs are prone to "syccophancy" (agreeing with the user).
- The "Critic" agent is the solution to this.